The Many Areas Of Information Security | Information Security Management Fundamentals Course
Summary
TLDRIn this video, the speaker provides an introduction to key concepts in information security management, emphasizing the breadth of the field. The lecture covers areas like application security, access control, business continuity, disaster recovery, and governance. It also touches on regulatory compliance, security architecture, network security, and cryptography. The speaker highlights the importance of the NIST Special Publication 800-53, a guide to best practices in the field, particularly for government agencies. The video serves as an overview for those new to the field, setting the stage for deeper exploration in future lectures.
Takeaways
- 🔐 Information security encompasses many areas, not just ethical hacking or network security.
- 🛠️ Application security focuses on secure development practices and testing to ensure security is integral to software creation.
- 🔑 Access control can be either physical or logical, involving both personnel and system administrators.
- 📈 Business continuity and disaster recovery are vital for ensuring operations continue after a disaster.
- 📋 Governance and risk management deal with policy creation, steering committees, and risk assessment (quantitative and qualitative).
- ⚖️ Legal, regulatory compliance, and investigations ensure that security practices follow laws and regulations, and address internal or external investigations.
- 🌐 Security architecture and design ensure security is built into the entire IT infrastructure, covering applications, networks, and systems.
- 🛡️ Network security involves firewalls, IDS/IPS systems, and incident response teams to monitor and protect network operations.
- 🔒 Physical security focuses on protecting the physical infrastructure, including buildings and access points.
- 🔑 Cryptography plays a crucial role in securing data through encryption and hashing, with professionals focused on algorithm development and testing.
Q & A
What is the main focus of this video lecture?
-The main focus of the video lecture is to introduce the different areas of information security and information security management. It aims to clarify common misconceptions and provide an overview of the broad field of information security.
What are some common misconceptions about information security that the speaker mentions?
-Some common misconceptions include thinking that information security only involves specific areas like ethical hacking, network security, or IT security operations. In reality, these are just small parts of the broader domain of information security and information security management.
What is application security, and what role does it play in information security?
-Application security involves securing the development lifecycle, ensuring secure coding practices are part of the development process, and not an afterthought. It also includes testing, accreditation, and certification of applications to ensure they meet security standards.
Can you explain the role of access control in information security?
-Access control in information security can be physical or logical. Physical access control deals with securing physical locations, while logical access control focuses on system and network access. Different personnel, such as system administrators, are responsible for ensuring secure access to these environments.
What is the significance of business continuity and disaster recovery in information security?
-Business continuity and disaster recovery are critical aspects of information security. They ensure that, in the event of a disaster, an organization has plans in place to continue operations and recover quickly. Specialized teams focus on developing, testing, and maintaining these plans.
What does governance and risk management involve?
-Governance and risk management involve setting policies and procedures, working with C-level executives to shape an organization's information security strategy, and managing risks by assessing their severity and implementing control measures to mitigate them.
What role do legal, regulatory compliance, and investigations play in information security?
-Legal and regulatory compliance ensures that organizations adhere to relevant laws and regulations in information security. Investigations, whether internal or in cooperation with law enforcement, are necessary to address any security incidents or breaches.
What is the purpose of the NIST Special Publication 800-53 mentioned in the video?
-The NIST Special Publication 800-53 provides best practices and guidelines for information security management. Although it is designed for the U.S. federal government, it can be used by other organizations, including state agencies, non-governmental organizations, and businesses, to enhance their security programs.
Who is the intended audience for the NIST Special Publication 800-53?
-The intended audience for the NIST Special Publication 800-53 includes agency heads, Chief Information Officers (CIOs), Chief Information Security Officers (CISOs), security managers, and anyone involved in implementing or overseeing information security programs.
How can the NIST guidelines help organizations outside the federal government?
-Although the NIST guidelines are designed for the U.S. federal government, they can help other organizations establish consistent information security practices. These guidelines provide a framework for improving security management programs across various industries and governmental bodies globally.
Outlines

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードMindmap

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードKeywords

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードHighlights

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードTranscripts

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレード関連動画をさらに表示

PENGANTAR MANAJEMEN PROYEK SISTEM INFORMASI | Pertemuan 2

ISO 27001 Risk Assessment: The Ultimate Guide
MCP-UNIT-1-MANAGEMENT CONCEPT & PRACTICES (MCP) TOPIC-UNIT-1 Lacture by Harshita Mam
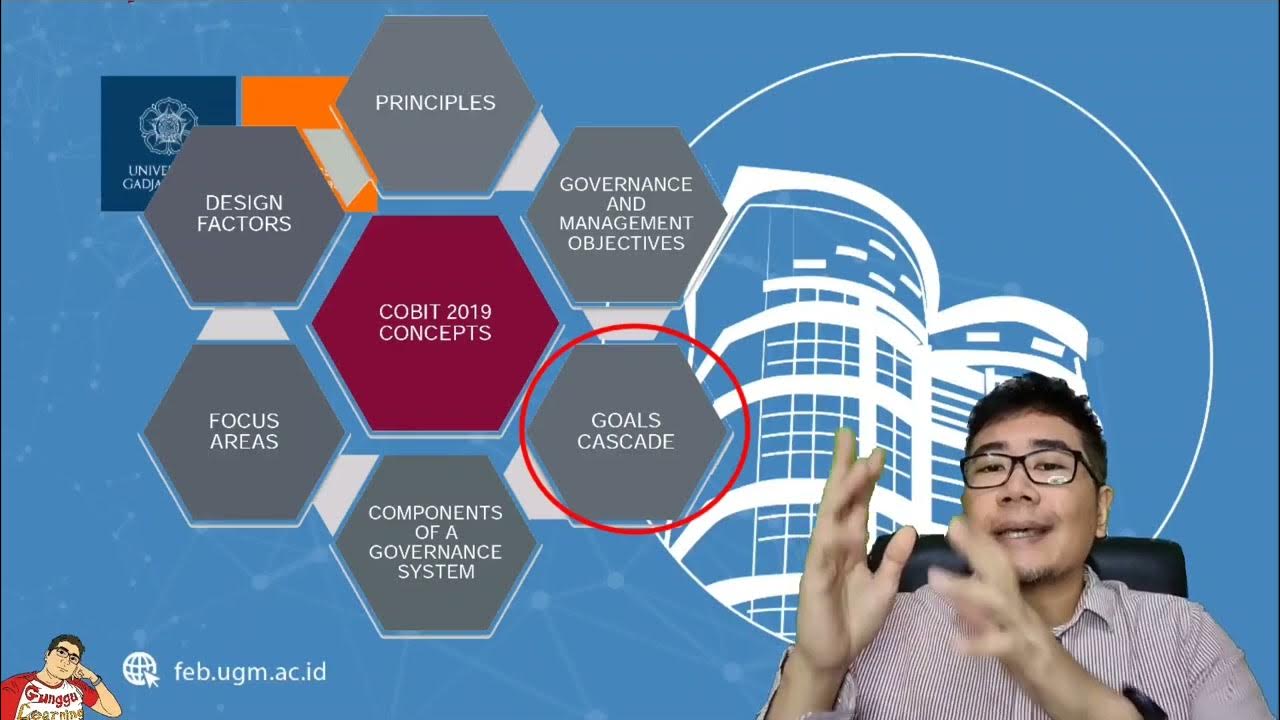
Information Systems Auditing 3b - Information Technology Governance Control (COBIT Framework)

DSA 1.4 Arrays: Single & Multidimensional Array with Examples
#1 Sistem Informasi Akutansi dan Keuangan - Pertemuan 1 | Konsep Dasar Sistem Informasi
5.0 / 5 (0 votes)
