SHA 256 | SHA 256 Algorithm Explanation | How SHA 256 Algorithm Works | Cryptography | Simplilearn
Summary
TLDRThis video delves into Secure Hash Algorithms (SHA), crucial for secure communication in the digital age. It explains hashing's role in scrambling data irreversibly and the SHA family's evolution from SHA-0 to SHA-3. The script outlines how hashing secures passwords, verifies data integrity, and is integral to digital signatures and SSL handshakes. It also details the SHA algorithm's process, from padding messages to generating digests, emphasizing its security against brute force attacks.
Takeaways
- 📝 Hashing is the process of transforming data into a scrambled format using algorithms to ensure data security.
- 💲 The primary difference between hashing and encryption is that hashing is irreversible, meaning the original data cannot be retrieved from the hash.
- 💵 Hash functions like SHA are crucial for secure communication and data transmission, playing a significant role in modern technology.
- 💲 Websites commonly use hashing to store user passwords securely, preventing plain text passwords from being exposed.
- 💵 Hashing verifies data integrity by comparing hash values before and after data transmission, ensuring the data has not been altered.
- 💲 The SHA (Secure Hash Algorithm) family, developed by NIST and NSA, includes SHA-0, SHA-1, SHA-2, and SHA-3, each with varying bit lengths and security features.
- 💵 SHA-256 and SHA-512 are part of the SHA-2 family, with SHA-256 using 32-bit words and SHA-512 using 64-bit words, offering different levels of security.
- 💲 SHA-3 was chosen after a public competition and differs significantly in structure from the other SHA family members, providing enhanced security.
- 💵 The SHA algorithm involves several steps including padding the message, initializing variables, processing blocks, and iterating through rounds to produce a hash digest.
- 💲 Hash functions are designed to be irreversible and resistant to collisions, making them essential for secure storage and transmission of sensitive data.
Q & A
What is the primary purpose of hashing?
-The primary purpose of hashing is to scramble a piece of information or data beyond recognition using hash functions, which are algorithms that perform mathematical operations on the original plain text.
How does hashing differ from encryption?
-Hashing differs from encryption in that hashes are irreversible; no decryption key can convert a digest back to its original plain text value.
What is the Secure Hash Algorithm (SHA) family?
-The Secure Hash Algorithm family is a set of cryptographic hash functions published by the National Institute of Standards and Technology along with the NSA.
What are the different families of hash functions within the SHA family?
-The SHA family includes SHA-0 (160-bit), SHA-1 (160-bit), SHA-2 (with functions like SHA-256 and SHA-512), and SHA-3 (also known as Keccak).
How does the SHA algorithm ensure data integrity?
-SHA algorithms ensure data integrity by generating a fixed-size hash value (digest) from variable-sized data, which can be compared before and after data transit to verify that the data has not been corrupted.
Why is hashing used for storing passwords?
-Hashing is used for storing passwords to prevent plain text passwords from being stored on servers, thereby enhancing security and protecting user privacy in the event of a data breach.
What is the significance of the padding process in the SHA algorithm?
-The padding process in the SHA algorithm ensures that the plain text message is compatible with the hash function by making the total number of bits a multiple of 512, which is necessary for the hashing process.
How does the SHA algorithm handle different lengths of plain text?
-The SHA algorithm handles different lengths of plain text by padding the message to ensure the total number of bits is a multiple of 512, and then processing the message in 512-bit blocks.
What are the characteristics that SHA family functions must follow while generating a digest?
-SHA family functions must ensure that the digest appears random, is irreversible, and that even a slight change in the plaintext triggers a drastic difference in the digest to prevent hash collisions.
How does the SHA algorithm contribute to secure web browsing sessions?
-The SHA algorithm contributes to secure web browsing sessions by being part of the SSL handshake process, which involves agreeing on encryption keys and hashing authentication to prepare a secure connection between web browsers and servers.
What are the advantages of using SHA hash algorithms over storing data in plain text?
-Using SHA hash algorithms over plain text storage provides advantages such as enhanced security through irreversible hash values, protection against data tampering, and the ability to verify the authenticity of digital signatures.
Outlines

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードMindmap

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードKeywords

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードHighlights

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードTranscripts

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレード関連動画をさらに表示
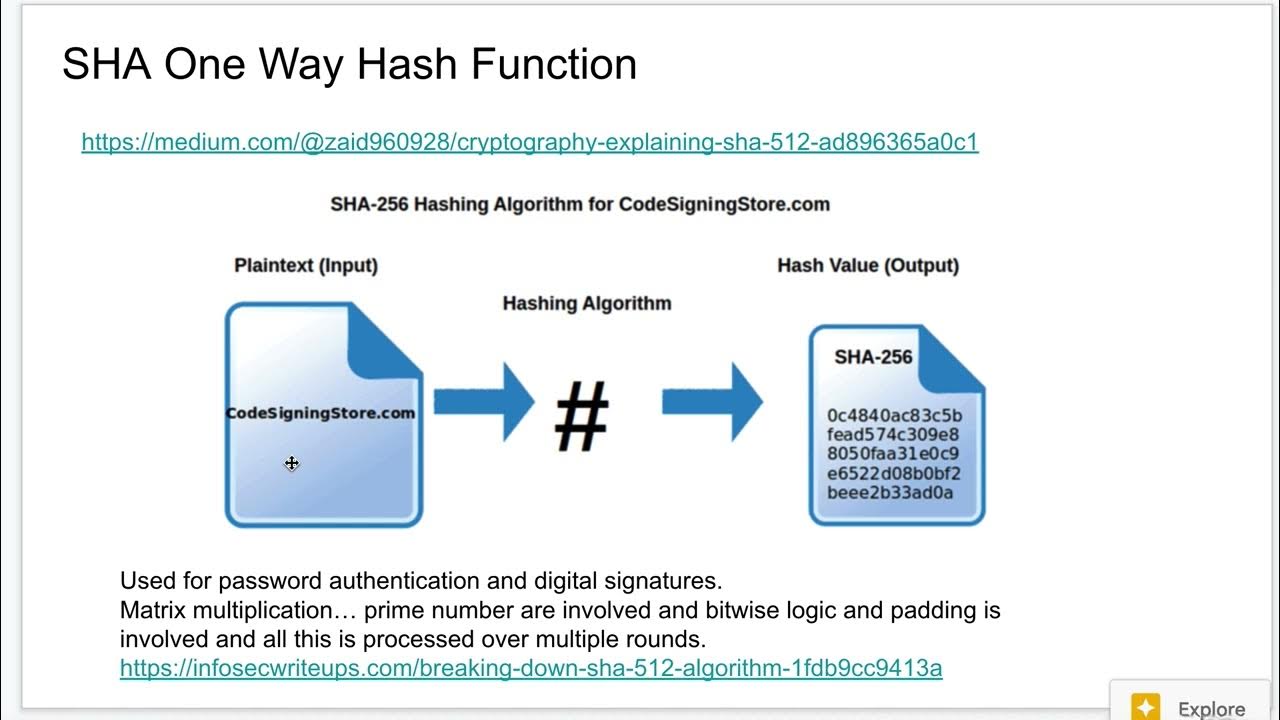
One Way Hash Explained

Digital Signatures and Digital Certificates

Hashing and Digital Signatures - SY0-601 CompTIA Security+ : 2.8
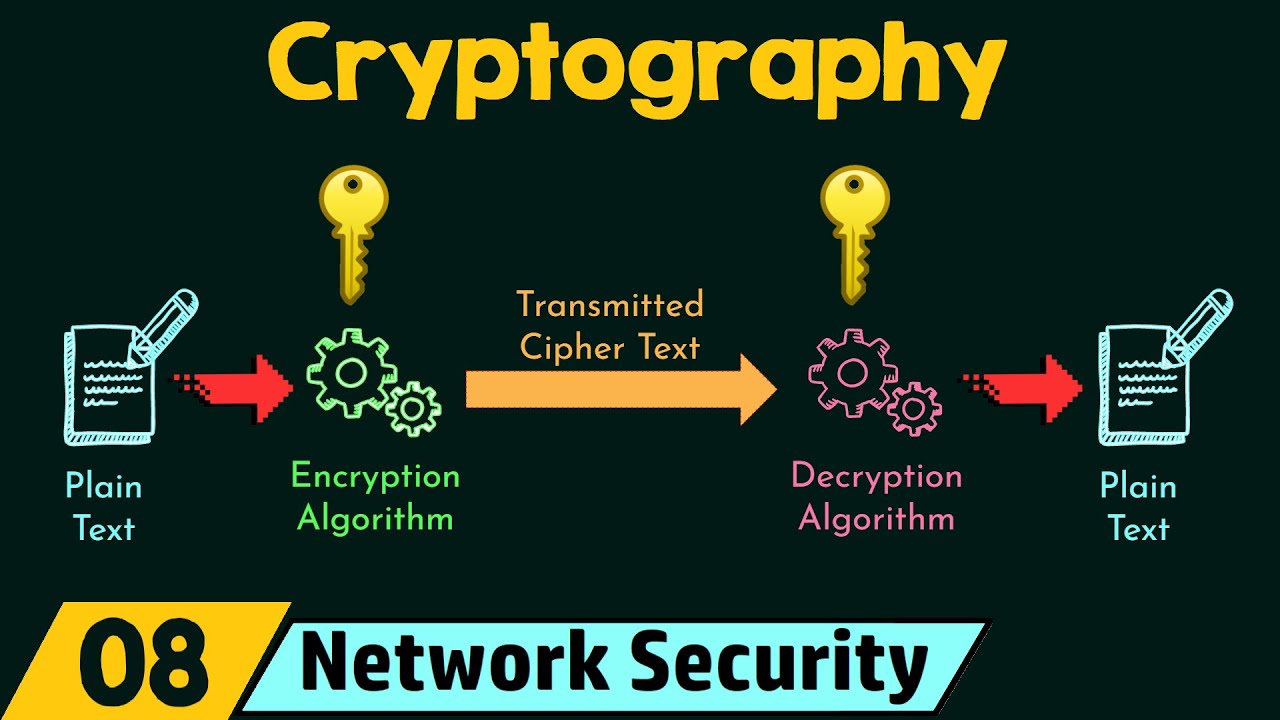
Cryptography

CompTIA Security+ SY0-701 Course - 1.4 Use Appropriate Cryptographic Solutions - PART A

Kripto 13: Kriptografi modern (Bagian 1: Representasi bit dan operasi XOR)
5.0 / 5 (0 votes)
