Chapter #8 - Cloud IAM Basics | identity & access management on google cloud platform (gcp)
Summary
TLDRThis video from 'itk funday' delves into the concept of Cloud IAM, or Identity and Access Management, on Google Cloud. It explains how IAM determines user permissions across cloud resources, using a relatable analogy of access levels in a company. The video covers the basics of IAM, including identities like Google accounts and service accounts, roles ranging from primitive to custom, and the importance of adhering to the principle of least privilege. It also touches on resource hierarchy and best practices for secure IAM policy management, providing a foundational understanding applicable to various cloud platforms.
Takeaways
- 😀 Identity and Access Management (IAM) is crucial for controlling who can do what on cloud resources, including Google Cloud Platform (GCP).
- 🔐 IAM consists of three main components: identity, role, and resource, which define who can access what resources and what actions they can perform.
- 👤 Identities in GCP can be a Google account, service account, Google group, or a Cloud Identity, each with different access levels and purposes.
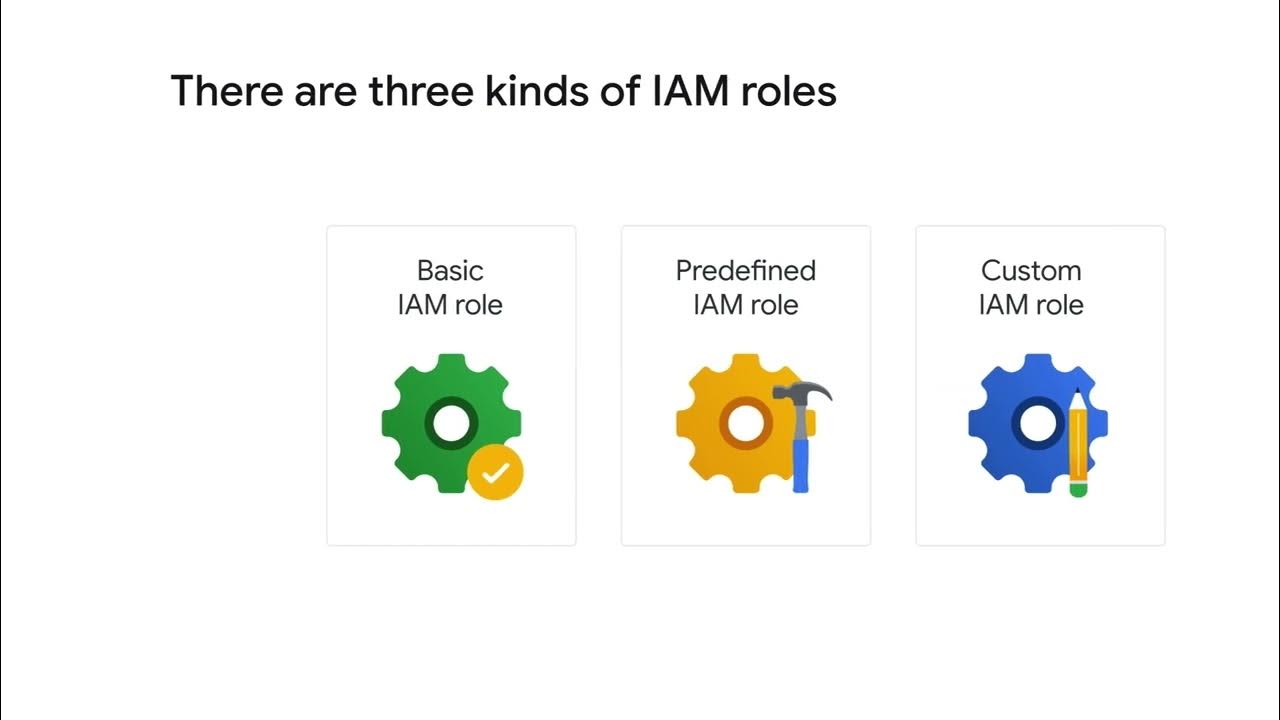
- 📋 Roles in IAM categorize into three types: primitive roles (owner, editor, viewer), predefined roles, and custom roles, with increasing specificity and control.
- 👷♂️ Primitive roles are broad and should be avoided in production environments due to security risks, instead, predefined or custom roles are recommended.
- 📝 Predefined roles offer a more specific set of permissions tailored to certain tasks, reducing the risk of over-privileging users.
- 🛠 Custom roles allow for the creation of highly specific permissions, useful for scenarios where predefined roles are too broad.
- 🏢 The concept of resource hierarchy in GCP is similar to real-world access control, where higher-level roles can inherit permissions to lower levels.
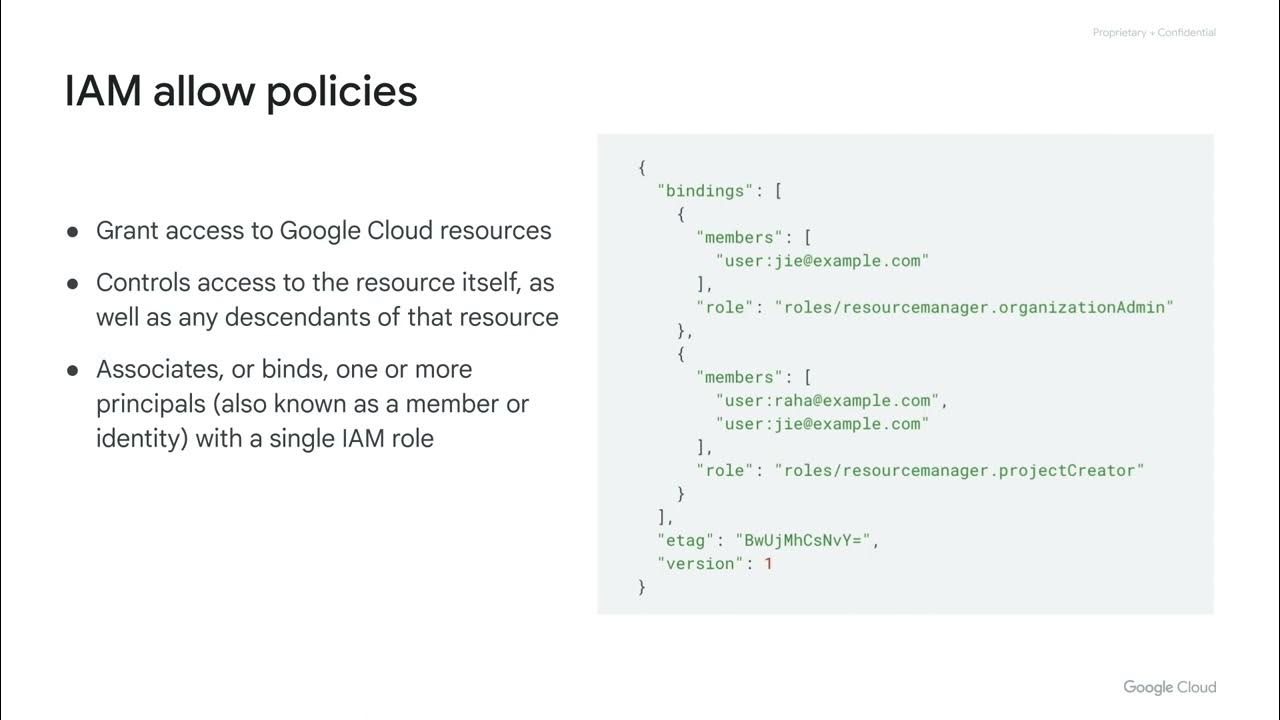
- 📍 IAM policies are binding and can be managed by IAM admins, combining members with their respective roles to control access.
- ⚠️ Best practices in IAM include avoiding primitive roles in production, adhering to the principle of least privilege, and managing IAM policies carefully.
- 📚 Further exploration of IAM on GCP and other cloud platforms is encouraged through the provided documentation link for a deeper understanding.
Q & A
What is the main focus of the video script?
-The main focus of the video script is to explain the concept of Identity and Access Management (IAM) on Google Cloud and how it works.
What are the three major parts of IAM according to the script?
-The three major parts of IAM are: determining who (identity), what they can do (permissions), and on which resources they can perform actions.
Can you explain the analogy of a visitor ID card in the context of IAM?
-The analogy of a visitor ID card in IAM is used to illustrate how access is limited based on the identity and role of an individual. A visitor ID card allows access to certain areas of an office, similar to how IAM restricts access to cloud resources based on assigned roles.
What is the significance of the principle of least privilege (PLP) in IAM?
-The principle of least privilege (PLP) in IAM ensures that users are given the minimum level of access necessary to perform their tasks, thereby enhancing security by limiting potential damage from user errors or malicious activities.
What are the different types of identities mentioned in the script for accessing Google Cloud resources?
-The different types of identities mentioned are Google accounts, service accounts, Google groups, and Cloud Identity. Each serves a different purpose and level of access within Google Cloud.
How do roles in IAM determine the set of permissions a user has?
-Roles in IAM are sets of permissions that define what actions a user can perform on certain resources. When a role is assigned to an identity, it grants the user the permissions bundled within that role.
What are the three categories of roles discussed in the script?
-The three categories of roles discussed are primitive roles (owner, editor, viewer), predefined roles, and custom roles. Primitive roles are broad, predefined roles offer a more specific set of permissions, and custom roles allow for the most granular control.
Why should primitive roles be avoided in production environments according to the script?
-Primitive roles should be avoided in production environments because they are very broad and can potentially violate the principle of least privilege by granting more access than necessary, which can pose security risks.
What is the resource hierarchy in Google Cloud, and how does it affect access control?
-The resource hierarchy in Google Cloud includes organizations, folders, projects, and resources like Compute Engine instances or storage buckets. Access control is affected because permissions can be inherited from higher levels in the hierarchy, and assigning roles at a higher level can grant broader access.
What are some best practices suggested by Google for managing IAM policies?
-Some best practices for managing IAM policies include avoiding primitive roles in production, adhering to the principle of least privilege, and using IAM policies to manage permissions at the appropriate level of the resource hierarchy.
Outlines

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantMindmap

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantKeywords

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantHighlights

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantTranscripts

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenant5.0 / 5 (0 votes)