Members
Summary
TLDRThe video script discusses Google Cloud's Identity and Access Management (IAM), focusing on member types like Google Accounts, Service Accounts, Google Groups, Workspace domains, and Cloud Identity domains. It explains IAM policies, the importance of the principle of least privilege, and how to manage permissions with role recommendations and policy insights. The script also covers deny policies, conditions, organization policies, and tools for integrating existing corporate directories with Google Cloud for seamless user and group management.
Takeaways
- 👤 Google Accounts are for individuals like developers or administrators and can be identified by any email address, even without using Gmail.
- 🔑 Service Accounts represent applications rather than individuals, allowing you to specify the identity under which your code runs on Google Cloud.
- 👥 Google Groups are collections of Google and service accounts with a unique email address, making it easy to manage access for multiple users at once.
- 🏢 Workspace domains are for organizations, representing all Google accounts within an organization and allowing new accounts to be created within this domain.
- 🌐 Cloud Identity provides similar capabilities to Workspace domains but without the collaboration tools like Gmail, Docs, etc.
- 🚫 IAM policies cannot be used to create or manage users or groups; instead, Cloud Identity or Workspace should be used for these tasks.
- 🔒 IAM policies consist of bindings that link members to roles, which are lists of permissions defined by IAM.
- 📋 The IAM policy hierarchy follows the Google Cloud resource hierarchy, meaning changes to the resource hierarchy affect the policy hierarchy.
- 🛑 Child policies cannot restrict more than parent policies, emphasizing the importance of the principle of least privilege in access control.
- 🔎 Role recommenders and policy insights help in identifying and removing excess permissions, enforcing the principle of least privilege at scale.
- 🏷️ IAM Conditions allow for conditional access control based on specific attributes, providing flexibility in granting permissions.
- 📝 Organization policies apply restrictions across the organization, folders, or projects, with inheritance down the resource hierarchy.
- 🔄 Google Cloud Directory Sync synchronizes existing corporate directories with Cloud Identity, facilitating the use of familiar credentials for Google Cloud access.
- 🔒 Single sign-on (SSO) allows for the use of existing identity systems with Google Cloud, providing a seamless authentication experience.
Q & A
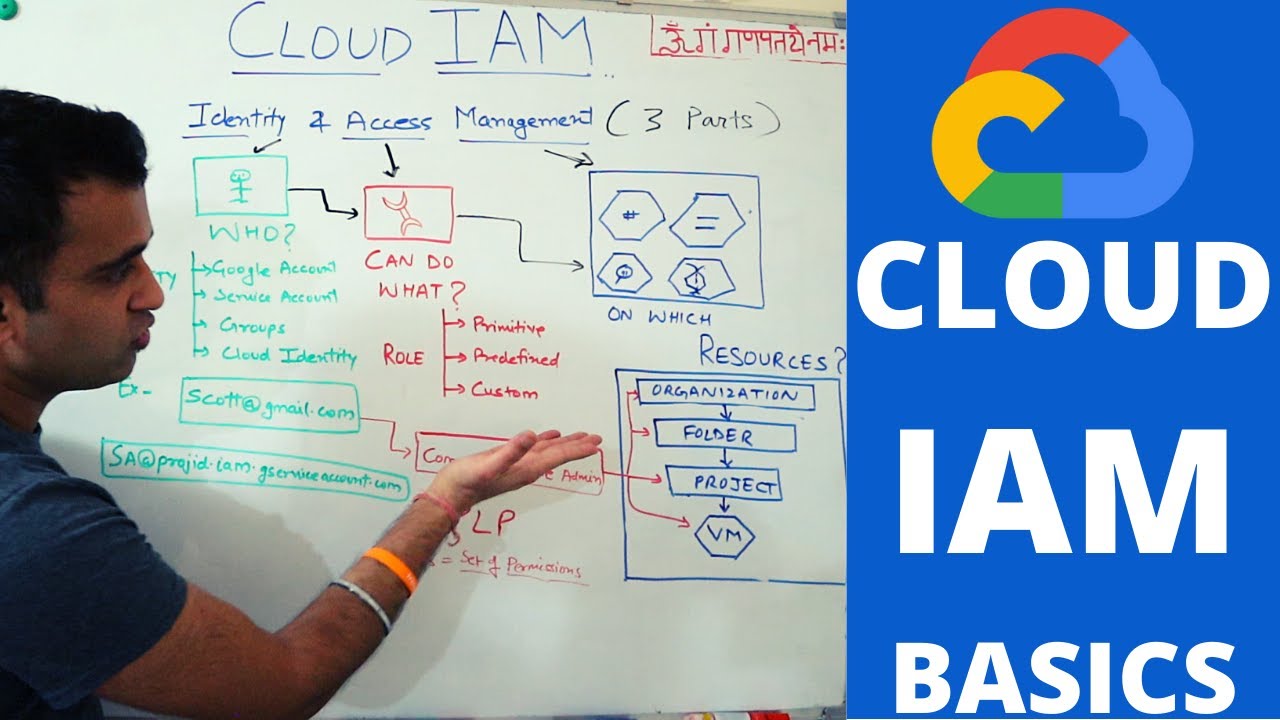
What are the five types of members in Google Cloud?
-The five types of members in Google Cloud are Google Accounts, Service Accounts, Google Groups, Google Workspace domains, and Cloud Identity domains.
What is a Google Account and how can it be used in Google Cloud?
-A Google Account represents a developer, an administrator, or any other person who interacts with Google Cloud. Any email address associated with a Google Account can be an identity, and new users can sign up for a Google Account without receiving mail through Gmail.
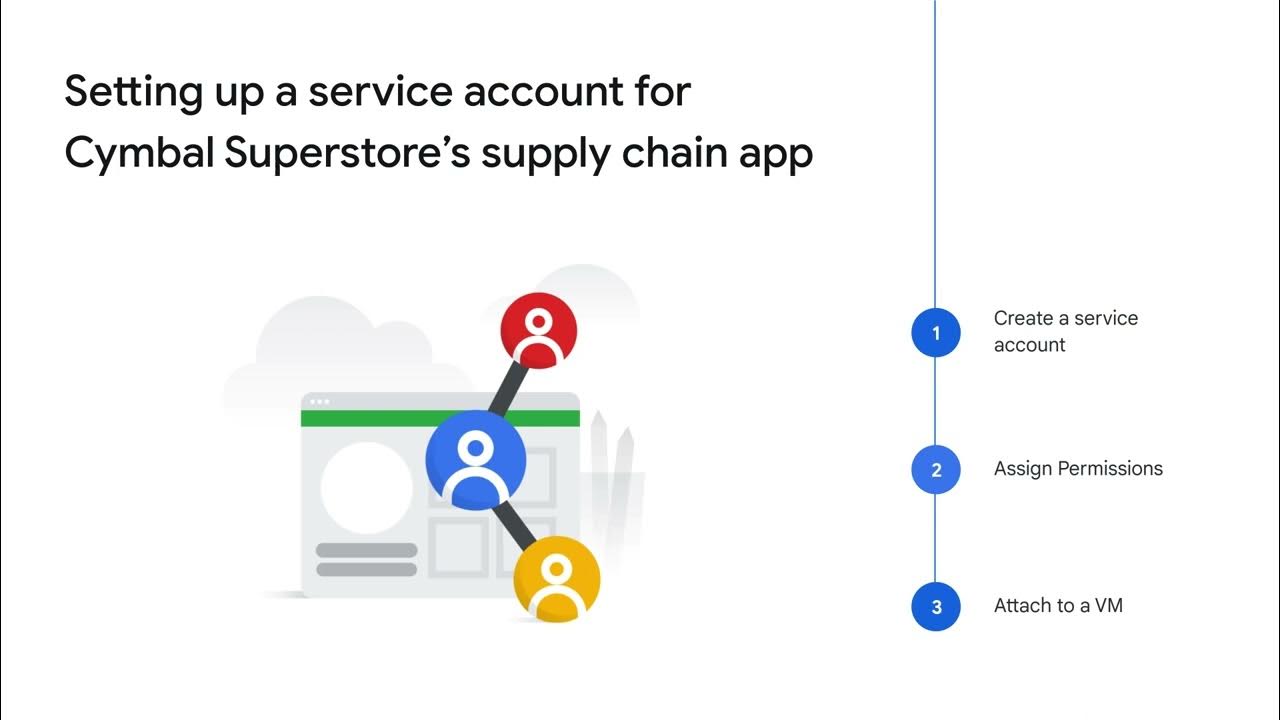
What is the purpose of a Service Account in Google Cloud?
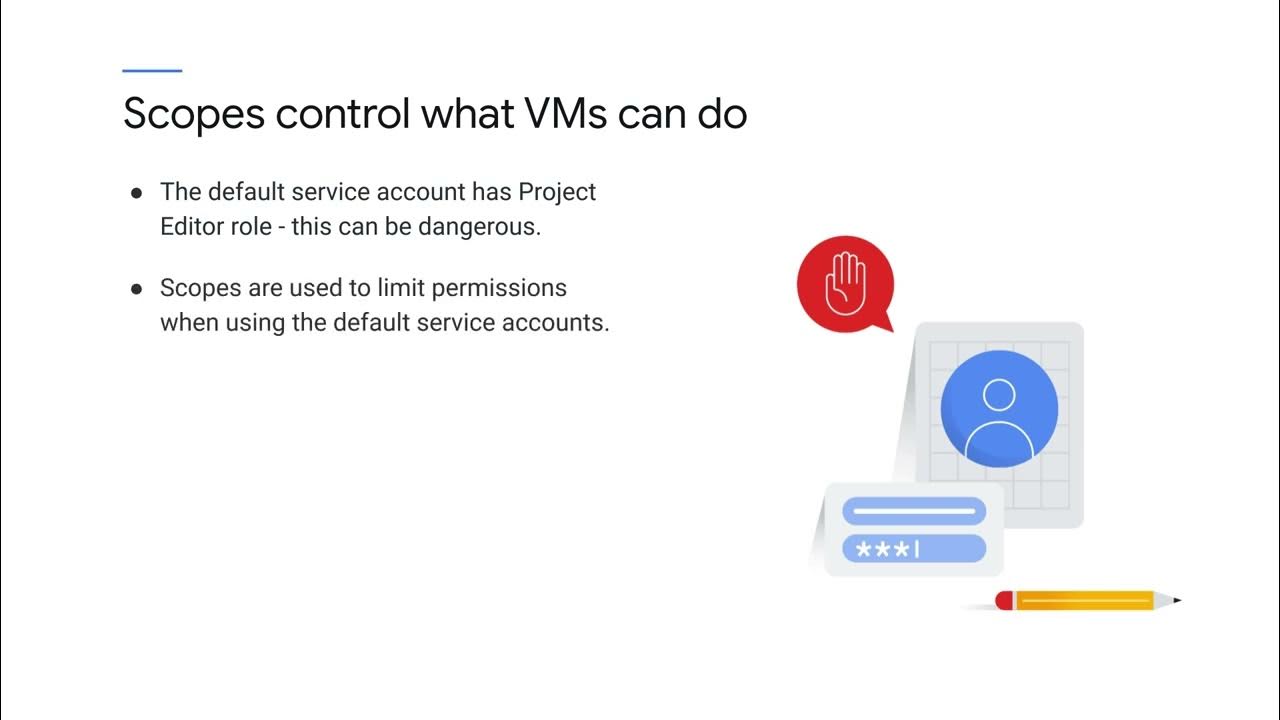
-A Service Account is an account that belongs to an application rather than an individual end user. It is used when running code on Google Cloud to specify the account that the code should run as.
How does a Google Group facilitate access control in Google Cloud?
-A Google Group is a named collection of Google Accounts and Service Accounts with a unique email address. It allows applying an access policy to a collection of users, enabling the granting and changing of access controls for a whole group at once instead of individual users or service accounts.
What is the role of a Workspace domain in Google Cloud?
-A Workspace domain represents a virtual group of all the Google Accounts created in an organization's Workspace account. It represents the organization's internet domain name, and new Google Accounts are created for users within this virtual group.
How does Cloud Identity differ from Google Workspace for non-Workspace customers?
-Cloud Identity allows non-Workspace customers to manage users and groups using the Google Admin Console without paying for or receiving Workspace's collaboration products such as Gmail, Docs, Drive, and Calendar.
What is the purpose of an IAM policy in Google Cloud?
-An IAM policy is a collection of access statements attached to a resource. It contains a set of roles and role members, with resources inheriting policies from their parent, and helps in defining who can do what on which resource.
How does the principle of least privilege apply to IAM in Google Cloud?
-The principle of least privilege in IAM suggests that identities, roles, and resources should always select the smallest scope necessary for the task to reduce exposure to risk. It helps enforce security by ensuring that principals have only the permissions they actually need.
What is the role of a recommender in IAM for role management?
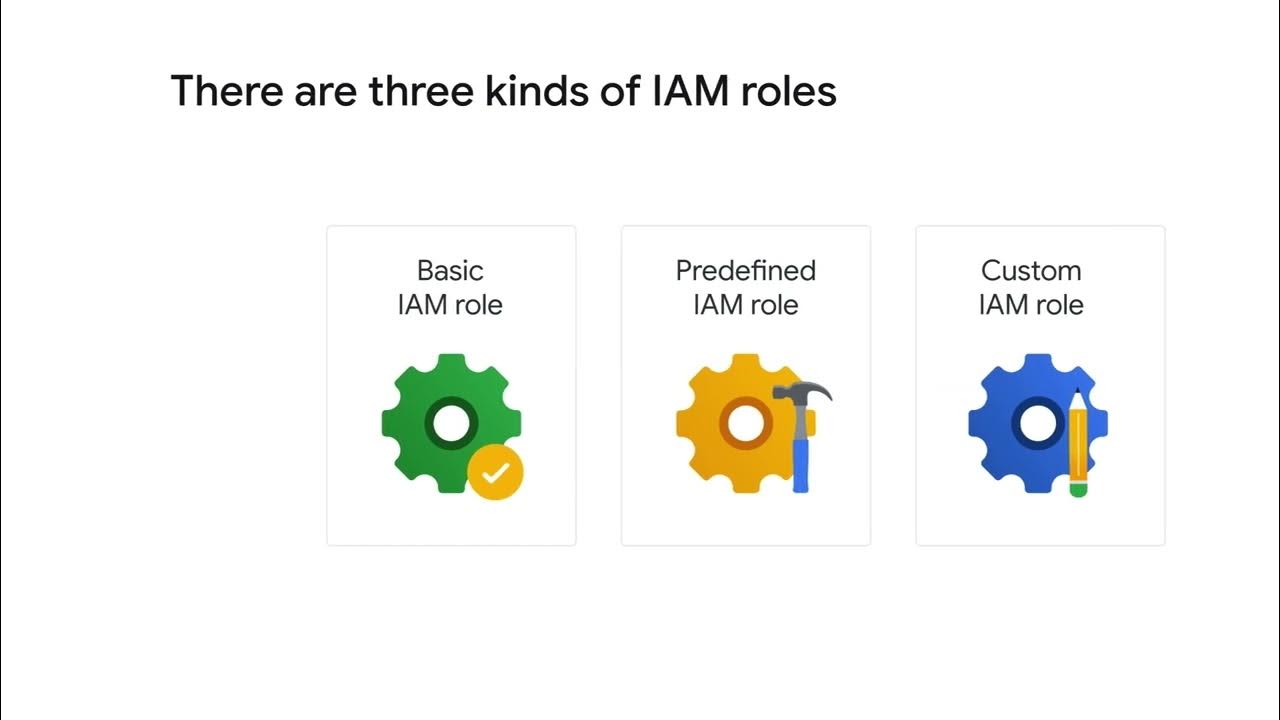
-A recommender in IAM provides role recommendations to identify and remove excess permissions from principals, improving security configurations by ensuring that principals have only the necessary permissions.
How do IAM Conditions work in Google Cloud?
-IAM Conditions allow for conditional, attribute-based access control. They define and enforce access to identities (members) only if configured conditions are met, allowing for temporary access or limiting access based on specific attributes.
What is an organization policy and how is it applied in Google Cloud?
-An organization policy is a configuration of restrictions applied to the organization node and all of its folders or projects. It is inherited by descendant resources in the hierarchy, and exceptions can be made by users with the organization policy admin role.
How can existing corporate directories be integrated with Google Cloud?
-Google Cloud Directory Sync allows administrators to manage Google Cloud resources using existing Active Directory or LDAP systems. It synchronizes users and groups one-way from the corporate directory to the Cloud Identity domain.
What is single sign-on (SSO) and how can it be configured for Google Cloud?
-Single sign-on (SSO) allows users to authenticate once in their identity system and then access Google Cloud without additional sign-in prompts. If the existing authentication system supports SAML2, SSO configuration involves setting up three links and a certificate. Otherwise, third-party solutions like ADFS, Ping, or Okta can be used.
Outlines

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantMindmap

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantKeywords

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantHighlights

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantTranscripts

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantVoir Plus de Vidéos Connexes
Chapter #8 - Cloud IAM Basics | identity & access management on google cloud platform (gcp)
Managing access for Cymbal Superstore’s cloud solutions
Authentication and authorization with IAM
Service accounts, IAM roles, and API scopes

The shared security model

01. GCP using Python SDK : How to access Cloud Storage using Service account ?
5.0 / 5 (0 votes)
