What is a Cryptographic Hashing Function? (Example + Purpose)
Summary
TLDRThis video from Whiteboard Crypto demystifies cryptographic hashing functions, using the SHA-256 algorithm as an example. It explains how these functions consistently produce a fixed-size output from any input, are quick to compute, and are irreversible and collision-resistant. The video also connects hashing to cryptocurrency mining, particularly Bitcoin's proof-of-work system, illustrating the process of finding a hash with a specific pattern to validate transactions on the blockchain.
Takeaways
- 😀 Cryptographic hashing functions are simplified for understanding by using analogies and stories.
- 🔒 A hashing function is like a 'magical black box' that takes an input and outputs a fixed-size hash.
- 📝 Bitcoin uses the SHA-256 hashing function, which is part of the Secure Hashing Algorithm family.
- 🔢 The '256' in SHA-256 refers to the length of the output hash in bits, resulting in a 64-character hexadecimal string.
- 🔁 Hash functions always produce the same output for the same input, regardless of the input size.
- 🚀 Hash functions output a fixed-size result, ensuring consistency in the hash length.
- ⏱️ Hash functions are designed to be quick to compute, enabling efficient processing of data.
- 🔄 Small changes in the input result in a significantly different output, which is crucial for security.
- 🔒 It's nearly impossible to find two different inputs that produce the same hash output, known as a hash collision.
- 💾 Cryptographic hashing is integral to the proof of work system used in mining Bitcoin.
- 🏭 The mining process involves adding transactions to the blockchain by finding a hash with a certain number of leading zeros.
Q & A
What is a cryptographic hashing algorithm?
-A cryptographic hashing algorithm is a system that takes an input (or 'message') and returns a fixed-size string of characters, which is typically a digest that is unique to the input. It's often referred to as a 'magical black box' in the script.
Why are hashing functions important in the context of cryptocurrencies?
-Hashing functions are crucial in cryptocurrencies because they are used in the proof-of-work system, which is the method used to mine new bitcoins and secure the blockchain against fraudulent transactions.
What does SHA-256 stand for, and what is its significance in Bitcoin?
-SHA-256 stands for Secure Hashing Algorithm 256. It is significant in Bitcoin because it is the hashing function used to secure transactions and create new blocks in the blockchain.
What are the five main properties of a hashing function as described in the script?
-The five main properties are: 1) Consistency in output for the same input, 2) Fixed-size output regardless of input size, 3) Quick computation, 4) Irreversibility and unpredictability of the output from the input, and 5) Infeasibility of finding two different inputs that produce the same output (low probability of hash collisions).
How does the size of the output of a hashing function relate to its security?
-The size of the output is directly related to the security of the hashing function. A larger output size, like the 256 bits in SHA-256, makes it computationally more difficult to find two inputs that produce the same hash, thus enhancing security.
Why is it necessary for a hashing function to be quick to compute?
-It is necessary for a hashing function to be quick to compute so that it can be used efficiently in systems where large volumes of data are processed, such as in cryptocurrency mining and blockchain transactions.
Can you reverse a hash to find the original input?
-No, due to the properties of cryptographic hashing functions, it is not feasible to reverse the hash to find the original input. This is known as the irreversibility of hashes.
What is a hash collision, and why is it significant in the security of hashing algorithms?
-A hash collision occurs when two different inputs produce the same hash output. It is significant for security because if collisions could be easily found, it would undermine the integrity and trustworthiness of the hashing algorithm.
How does the process of mining Bitcoin relate to the use of a cryptographic hashing function?
-Mining Bitcoin involves finding a hash that meets certain criteria, such as having a specific number of leading zeros. This process requires a lot of computational work, which is why it is called 'proof-of-work' and uses the SHA-256 hashing function.
What is the purpose of adding a random set of numbers and letters to the transaction list in the mining process?
-The random set of numbers and letters, often called a 'nonce', is added to vary the input to the hashing function. This is done to find a hash that meets the required difficulty criteria for mining a new block in the blockchain.
How does the script illustrate the concept of 'difficulty' in the mining process?
-The script illustrates the concept of 'difficulty' by showing how the mining process involves guessing and checking different inputs until a hash with a certain number of leading zeros is found, which becomes increasingly difficult as more zeros are required.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenWeitere ähnliche Videos ansehen
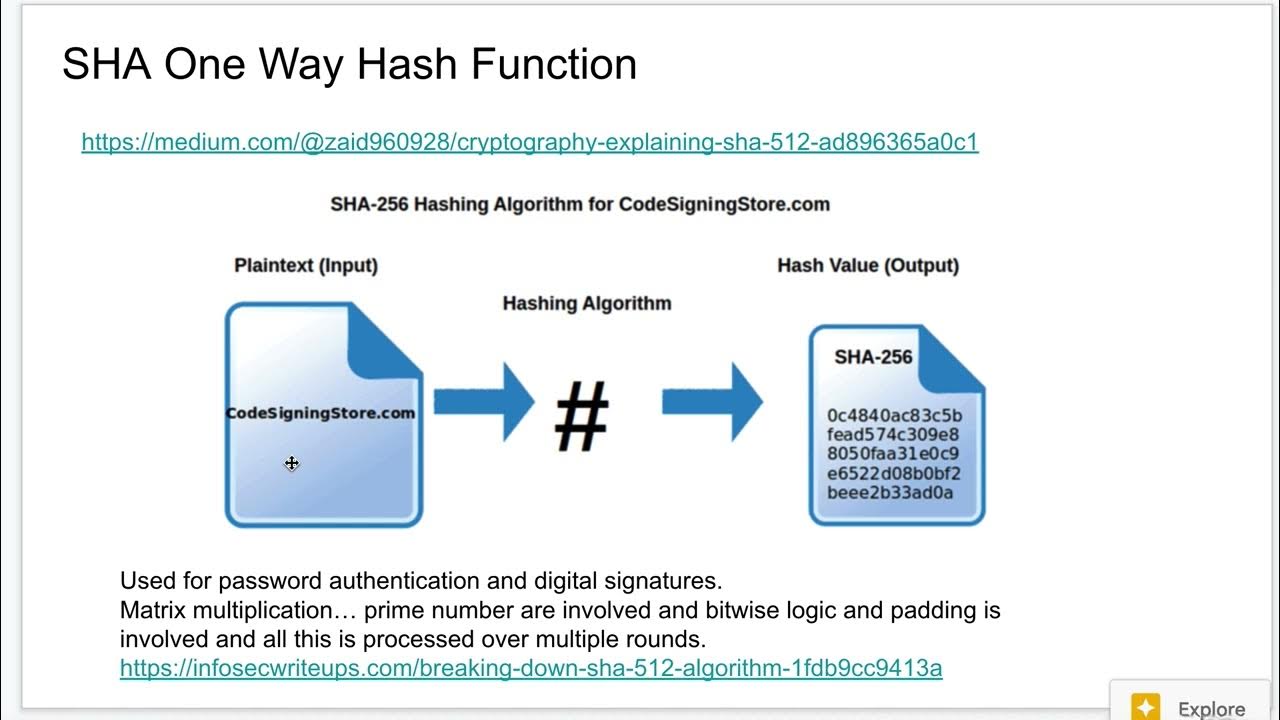
One Way Hash Explained

How secure is 256 bit security?

Blockchain Technology Explained | Blockchain Technology Tutorial | Blockchain Tutorial | Simplilearn

4.9.2 Secure Hash Algorithm Part 2 in Tamil

🔴 Build Your Own Blockchain | How to Create a Blockchain? | Blockchain Tutorial | Simplilearn

MD5 Algorithm | What Is MD5 Algorithm? | MD5 Algorithm Explained | Network Security | Simplilearn
5.0 / 5 (0 votes)
