HD 1080DPI 2 WiFi IoT Hacking Demo Guide
Summary
TLDRThis tutorial video demonstrates the use of the aircrack-ng suite on the Kali Linux platform for auditing wireless networks. It guides viewers through the process of finding a network's password using aircrack-ng tools, from creating a monitoring interface with airmon-ng to capturing traffic with airodump-ng, and ultimately cracking the WPA key with a wordlist. The video concludes with connecting to the secured network using the discovered passphrase, showcasing the importance of secure wireless implementation.
Takeaways
- 📹 This video demonstrates the use of the aircrack-ng suite for auditing wireless networks on the Kali Linux platform.
- 🗂️ Viewers are advised to take notes for future reference while completing the lab after watching the video.
- 📁 A directory is created in the root directory to store capture files for the wireless attack.
- 🔒 The airmon-ng tool is used to start a monitor mode interface for capturing wireless traffic and conducting attacks without prior network authentication.
- 🔎 The ifconfig command is used to verify the creation of the mon0 interface, which is essential for monitoring.
- 🚀 Airplay-ng is utilized to inject frames and generate traffic for cracking WEP and WPA PSK keys by deauthenticating clients and capturing their authentication information.
- 📡 Airodump-ng monitors a specific channel and access point, capturing all traffic into a file for later analysis.
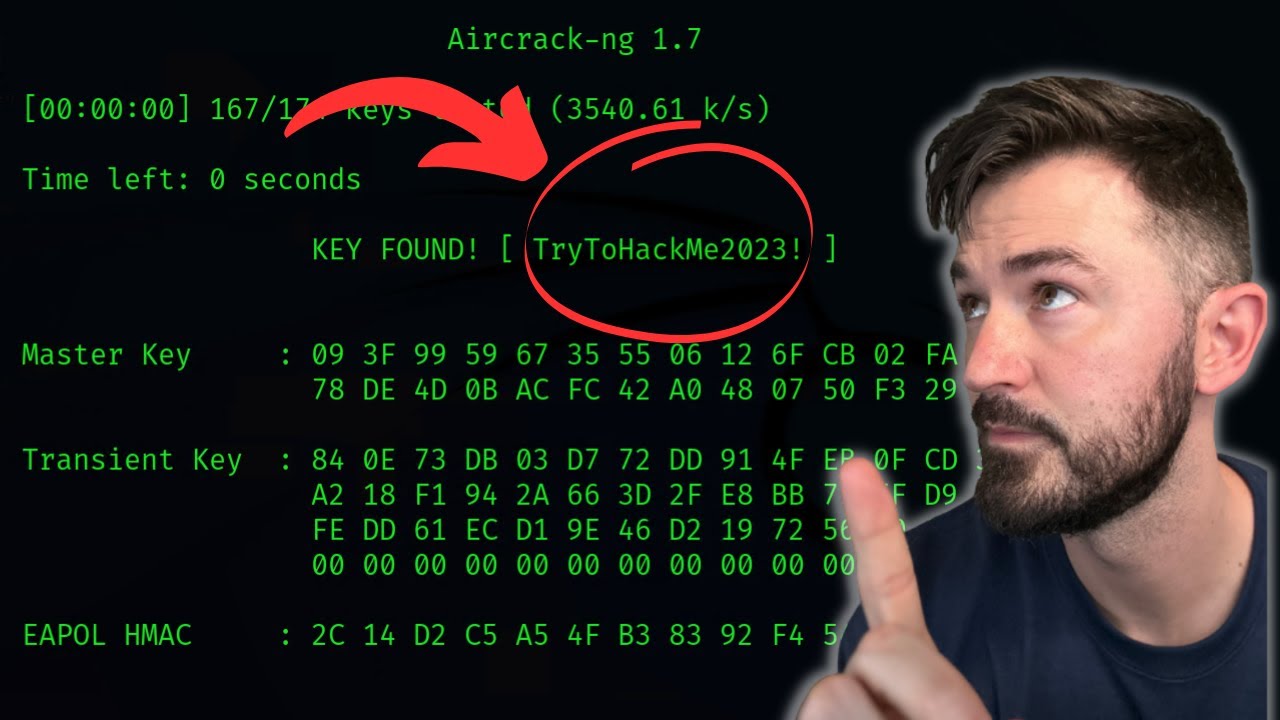
- ⏹️ The airodump-ng process is stopped using Ctrl+C, and then aircrack-ng is used with a wordlist to attempt to crack the network password.
- 🔑 Aircrack-ng presents a list of detected networks for selection, and it uses a dictionary attack to find possible passphrases.
- 🔍 Good wordlists can significantly reduce the time required to crack a network password, often within 10 minutes.
- 📡 After cracking the password, the airmon-ng stop command is used to stop the monitor mode interface.
- 🔗 Once the passphrase is obtained, it can be used to connect to the secured wireless network by entering it in the network manager.
Q & A
What is the purpose of the aircrack-ng suite of tools demonstrated in the video?
-The aircrack-ng suite is used for auditing wireless networks to find a wireless network password and log on to the secured wireless network.
Which platform is used for the penetration testing demonstration in the video?
-The Kali penetration testing platform is used for the demonstration.
What is the first step after logging into Kali in the demonstration?
-The first step is to make a directory to store the capture files.
What command is used to create a monitor mode interface for wireless traffic monitoring and attacks?
-The command 'airmon-ng start' is used to create a monitor mode interface.
How can you verify that the mon0 interface has been created?
-You can verify the creation of the mon0 interface by issuing the command 'ifconfig', which will show all interfaces.
What is the purpose of the airplay-ng tool in the context of the demonstration?
-The airplay-ng tool is used to inject frames to generate traffic that aircrack-ng will later use for cracking the WEP and WPA PSK keys.
What does the 'deauthentication attack' mentioned in the script do?
-A deauthentication attack forces clients off a given network, causing a denial of service (DoS) attack, which in turn forces the client to re-authenticate, allowing the capture of their authentication information.
How does airodump-ng capture traffic from a specific network?
-Airodump-ng captures traffic by monitoring a specific channel and using the MAC address of the target access point, then dumping all traffic into a file.
What is the command used to stop the airodump-ng process in the demonstration?
-The process is stopped by pressing 'control-c' in the airodump-ng terminal window.
How does aircrack-ng utilize a word list to find possible passphrases for a network?
-Aircrack-ng uses a word list or passphrase dictionary to search for possible passphrases against the capture files created by airodump-ng.
What is the final step to connect to the silent valor network after discovering the passphrase?
-The final step is to enter the discovered passphrase in the network properties dialog box, select WPA2 encryption, and click connect.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenWeitere ähnliche Videos ansehen

How to Use Wifite in Kali Linux: Automated Wireless Penetration Testing Tool

Perform Wireless Attacks | CEHv12 Practical ILabs Walkthrough

How Hackers Move Through Networks (with Ligolo)
[Solved] RTL8812AU wireless network interface cannot find available networks on Kali Linux
How To Crack WPA2 WiFi Password With AirCrack-NG - WiFi Pentesting Video 2024

Top 10 Hacking Tools for Beginners in Kali Linux 2025
5.0 / 5 (0 votes)
