What is a DMZ? (Demilitarized Zone)
Summary
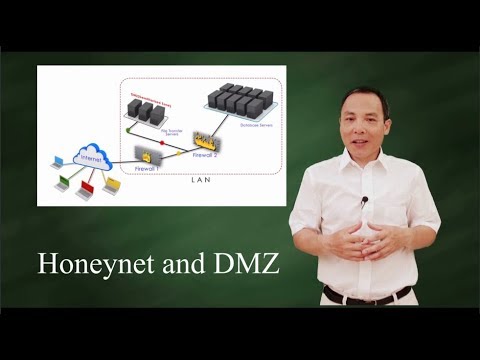
TLDRA DMZ (Demilitarized Zone) in networking is a security feature that separates public-facing servers, like web and email servers, from a company’s internal network. This minimizes security risks by isolating sensitive data behind firewalls, while allowing external access to these services. A secure DMZ setup may involve two firewalls for enhanced protection. In home networks, a DMZ can be configured through a router to expose specific devices, such as gaming consoles, to the internet without disrupting other devices behind the firewall. This setup ensures smooth, secure connections while maintaining privacy and safety for internal networks.
Takeaways
- 😀 DMZ stands for Demilitarized Zone and is used to improve the security of an organization's network by segregating devices behind firewalls.
- 😀 A DMZ creates two separate networks by placing certain devices, like web and email servers, on the opposite side of a firewall to protect internal resources.
- 😀 The main purpose of a DMZ is to allow external access to servers without exposing the organization's internal network to potential security threats.
- 😀 A common example of a DMZ is a web server or email server that needs to be accessed by people from the internet, while keeping internal data secure.
- 😀 Without a DMZ, external traffic accessing servers behind the firewall could open the door for hackers to penetrate into the internal network and compromise sensitive data.
- 😀 A DMZ can act like a perimeter network, screening malicious activity before it can breach the firewall and enter the internal network.
- 😀 The most basic DMZ setup uses a single firewall, but a more secure configuration employs two firewalls, adding an additional layer of protection.
- 😀 In a more secure DMZ setup, external traffic must pass through two firewalls, making it harder for hackers to reach the internal network.
- 😀 DMZ configurations are not limited to large networks but can also be applied to home routers, though this typically involves setting up a 'DMZ host' rather than a full DMZ.
- 😀 In home networks, devices like gaming consoles (e.g., Xbox or Playstation) can be designated as a DMZ host to avoid interference from the firewall, often used for online gaming.
- 😀 For home DMZ configurations, it’s essential to assign a static IP to the device in the DMZ for proper forwarding, as opposed to using dynamic IP addresses.
Q & A
What does DMZ stand for?
-DMZ stands for Demilitarized Zone, which in networking refers to a security zone that separates an organization's internal network from externally accessible servers or devices.
What is the main purpose of a DMZ in network security?
-The main purpose of a DMZ in network security is to segregate publicly accessible devices (like web and email servers) from sensitive internal systems, reducing the risk of unauthorized access to the internal network.
How does a DMZ improve network security?
-A DMZ improves security by placing public-facing servers outside the internal firewall. This prevents external threats from easily accessing the internal network, even if the public servers are compromised.
Why are servers like web servers and email servers placed in a DMZ?
-Web servers and email servers are placed in a DMZ because they need to be accessible from the internet, but placing them inside the internal network could expose sensitive data to external threats.
What could happen if these servers were not in a DMZ?
-If the servers were not in a DMZ, external attackers who compromise the servers could gain access to the internal network and potentially sensitive data, such as databases or private company information.
How does a DMZ with two firewalls offer enhanced security?
-A DMZ with two firewalls adds an extra layer of protection. One firewall separates the public-facing servers from the external internet, and the second firewall protects the internal network from being directly accessed, making it more difficult for attackers to penetrate.
How is a DMZ configured in a home network?
-In a home network, a DMZ is often configured through the router by designating a device (like a gaming console) as a DMZ host. This exposes the device directly to the internet, bypassing the router's firewall.
What is the purpose of placing a gaming console in a DMZ in a home network?
-The purpose of placing a gaming console in a DMZ is to avoid firewall interference during online gaming. This setup allows the console to have open internet access without the need for port forwarding configurations.
Why is it important to assign a static IP to a device in a home DMZ?
-It is important to assign a static IP to a device in a home DMZ to ensure that the device’s IP address remains the same, allowing the router to consistently forward all necessary ports to the correct device.
Is the DMZ configuration in a home router the same as in enterprise networks?
-No, the DMZ configuration in a home router is not the same as in enterprise networks. In home networks, it typically refers to designating a single device as a DMZ host, whereas in enterprise networks, a DMZ involves creating a separate security zone to protect sensitive internal systems.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführen5.0 / 5 (0 votes)