49. OCR A Level (H446) SLR9 - 1.3 Hashing
Summary
TLDRThis video explains the concept of hashing, a one-way function that converts input data into a fixed-length value or key, such as those generated by algorithms like SHA-1 and MD5. Unlike encryption, which allows for decryption, hashing ensures that the original data cannot be retrieved from the hash. The video highlights the practical applications of hashing in securing passwords during online sign-ups and improving data retrieval efficiency in data structures. By applying hashing, sensitive information remains protected, making it impossible for hackers to recover original passwords from stored hashes.
Takeaways
- 🔑 Hashing transforms a string of characters into a fixed-length value or key.
- 🛠️ Popular hashing algorithms include SHA-1 and MD5.
- 🔄 Hashing is a one-way process, meaning the original input cannot be derived from the hash value.
- 🔒 Hashing is ideal for protecting sensitive information like passwords and PINs.
- 👩🎓 During account creation, users should never have their passwords stored in plain text.
- 📡 When logging in, passwords are hashed and compared to stored hash values, preventing plaintext exposure.
- 🚫 Even if hashed passwords are intercepted, they cannot be reverse-engineered to retrieve the original password.
- ⚡ Hashing improves efficiency in searching, inserting, and deleting data from data structures.
- 📊 Hashing provides constant O(1) time complexity for data retrieval.
- 🔍 The video hints at further exploration of hash tables and algorithm time complexity in future content.
Q & A
What is hashing?
-Hashing is a process that transforms a string of characters into a fixed-length value or key, which represents the original input string using a hashing function.
How does a hashing function work?
-A hashing function uses an algorithm to convert input data into a hash value. Even a minor change in the input results in a completely different hash value.
What are some common hashing algorithms?
-Popular hashing algorithms include SHA-1 and MD5.
What is the main difference between hashing and encryption?
-The main difference is that hashing is a one-way process, meaning you cannot retrieve the original value from the hashed output, while encryption can be reversed to obtain the original data.
Why is hashing used for storing passwords?
-Hashing is used for storing passwords to ensure they are not kept in plain text. This protects the passwords from being exposed even if a hacker gains access to the stored data.
What happens when a user logs in and enters their password?
-When a user logs in, the system hashes the entered password and compares the hash value to the one stored in the database to verify the user's identity.
Can a hashed password be reverse-engineered?
-No, hashed passwords cannot be reverse-engineered to retrieve the original passwords due to the one-way nature of hashing.
How does hashing improve data structure operations?
-Hashing improves data structure operations by allowing for quick searching, insertion, and deletion of data. It eliminates the need for sorting or searching through data sequentially.
What is the time complexity benefit of using hashing?
-Hashing provides a constant average time complexity of O(1) for accessing data, making it very efficient.
What is the significance of the statement 'hashing provides a constant O(1) time complexity'?
-This means that hashing allows for very fast access to data, regardless of the size of the dataset, as it can retrieve information without searching through it linearly.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenWeitere ähnliche Videos ansehen
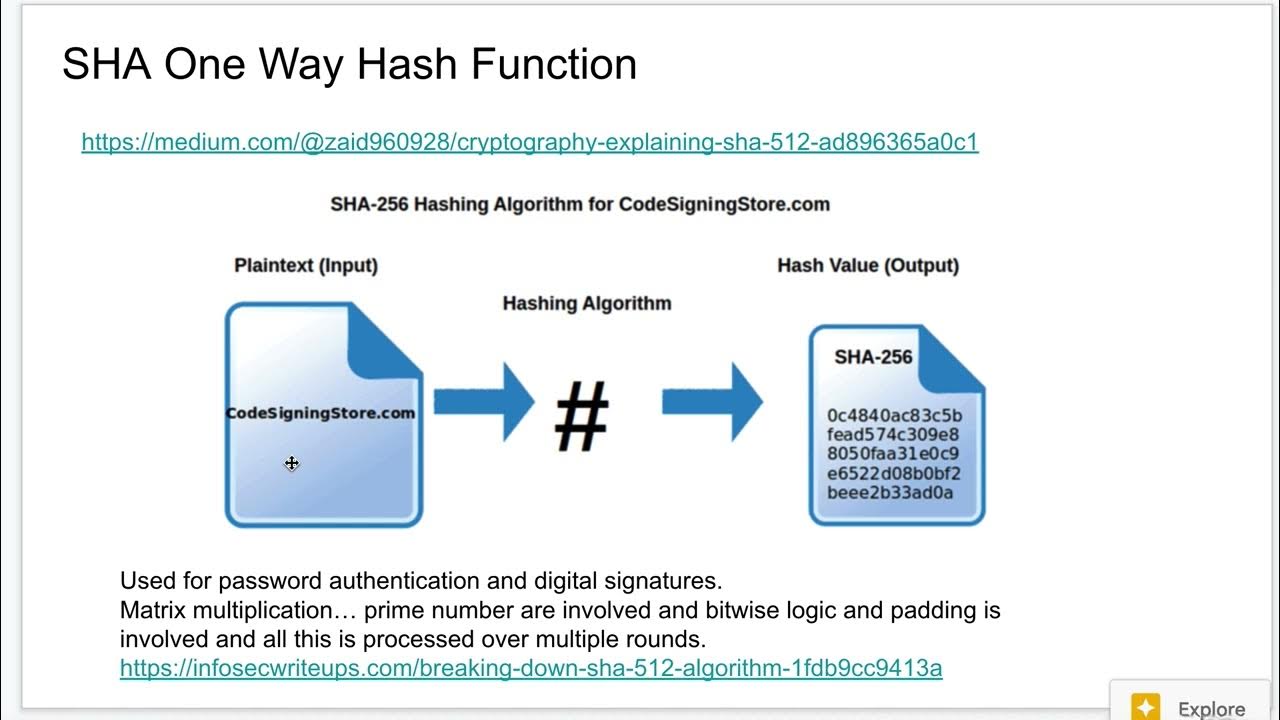
One Way Hash Explained

Hashing and Digital Signatures - SY0-601 CompTIA Security+ : 2.8

MD5 Algorithm | What Is MD5 Algorithm? | MD5 Algorithm Explained | Network Security | Simplilearn

Database Security - SY0-601 CompTIA Security+ : 3.2

Blockchain Hashing Explained! (You NEED to understand this)

SHA 256 | SHA 256 Algorithm Explanation | How SHA 256 Algorithm Works | Cryptography | Simplilearn
5.0 / 5 (0 votes)
