29C3: A Rambling Walk Through an EMV Transaction (EN)
Summary
TLDRThe speaker, Tim Becker, provides an in-depth analysis of the EMV (Europay, Mastercard, and Visa) protocol, which is the communication standard between chip-based credit cards and payment terminals. He discusses the history and technicalities of the protocol, highlighting its age and pragmatic design from the 1980s. Becker demonstrates how the protocol works at a low level, explaining the use of APDU (Application Protocol Data Units) for data exchange and the reliance on static data authentication. He also touches on the security aspects, including the potential for man-in-the-middle attacks and the fact that the data transmitted between the card and reader is unencrypted. The talk concludes with a live demonstration of interacting with a card using a card reader and custom Ruby code, emphasizing the accessibility of understanding and experimenting with EMV technology.
Takeaways
- 📍 EMV stands for Europay, Mastercard, and Visa, and it's a payment protocol that facilitates communication between a chip card and a payment terminal.
- 🔍 The presenter has extensive experience in credit card processing and fraud management, having worked at a German bank and a consultancy, and is currently an independent contractor.
- 💡 EMV technology is being mandated in the United States, which will lead to a significant increase in its usage, despite its age and known security shortcomings.
- 🛠 The session covered both basic and low-level aspects of EMV, including text, numbers, and technical specifications, without revealing secrets or sophisticated hacks.
- 💳 The presenter demonstrated how to use a card reader to interact with a chip card, showcasing that no special terminal is needed, and that the process is standardized and accessible.
- 🔗 PC/SC (PCSC) is the method used to connect a card reader to a computer, and most operating systems support it to some extent.
- 📚 ISO 7816 is the standard that defines the low-level characteristics of how the physical layer communicates with the card, which uses a simple serial interface.
- 🛂 APDU (Application Protocol Data Unit) is the method of exchanging packets between the card and the host, and it's a straightforward process of sending and receiving data bits.
- 🔐 The EMV protocol includes various security features such as key derivation, certificates, and data dictionaries, although not all cards use the most secure options like DDA (Dynamic Data Authentication).
- 📈 The general flow of EMV transactions includes card and terminal introduction, application selection, data verification, cardholder verification, and the generation of a cryptogram to validate the transaction.
- ⚠️ The EMV protocol has been criticized for its age and lack of robust security features, and these concerns are carried over to new technologies like contactless payments.
Q & A
What does EMV stand for and what is its purpose?
-EMV stands for Europay, Mastercard, and Visa. It is a global standard for credit and debit card transactions that defines the protocols between the chip on the card and the payment terminal.
What is the significance of the ATR (Answer to Reset) in the context of EMV?
-The ATR is a series of bytes sent by a smart card to the card reader after the card is powered up. It provides essential information for the terminal to communicate with the card, including the supported communication protocols and other settings.
What does PCSC stand for and what is its role in smart card communication?
-PCSC stands for PC/SC, which is a framework for smart card communication. It allows a smart card reader to communicate with a smart card when connected to a PC, enabling the card to be used for various applications.
What is APDU and how does it relate to EMV transactions?
-APDU stands for Application Protocol Data Unit. It is the format of the packets exchanged between the card and the host during an EMV transaction. APDUs carry the commands and data used in the transaction process.
What are the main components of the EMV specifications?
-The main components of the EMV specifications are divided into four books: Book 1 covers general information, Book 2 deals with cryptography, Book 3 specifies the APDUs and card commands, and Book 4 describes the card acceptance environment.
How does the EMV protocol handle security and authentication?
-The EMV protocol uses a combination of chip-based technology, cryptography, and secure messaging to ensure security and authentication. It includes features like static data authentication, dynamic data authentication, and cardholder verification methods.
What is the role of the issuer certificate in EMV transactions?
-The issuer certificate is used in EMV transactions to authenticate the card and ensure the data on the card is from a legitimate issuer. It contains the issuer's public key, which is used to verify a hash of the card's static data.
What is the significance of the AFL (Application File Locator) in an EMV card?
-The AFL is a list of file identifiers on the EMV card that tells the terminal which files to read during a transaction. It is crucial for the terminal to access the correct data, such as the cardholder name, account number, and other relevant information.
How does the EMV protocol handle cardholder verification?
-The EMV protocol provides several methods for cardholder verification, including PIN verification by the card, signature verification, and PIN verification by the bank. The terminal will attempt to use the most secure method supported by the card and available at the terminal.
What are the potential security weaknesses in the EMV protocol?
-Despite its security features, the EMV protocol has potential weaknesses, such as the lack of encryption in the communication between the card and the terminal, which makes it susceptible to man-in-the-middle attacks. Additionally, the reliance on static data authentication can make cards easier to clone.
How does the EMV protocol compare to magnetic stripe transactions in terms of security?
-The EMV protocol is designed to be more secure than magnetic stripe transactions due to its chip-based technology and cryptographic authentication. However, magnetic stripe data is still present on EMV cards, which can be read and potentially cloned, representing a weaker link in the security chain.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenWeitere ähnliche Videos ansehen

Everything you need to know about EMV | emerchantpay

Visa & Mastercard STOCK CRASH – Is This the Best Time to BUY?

The Future of Payments
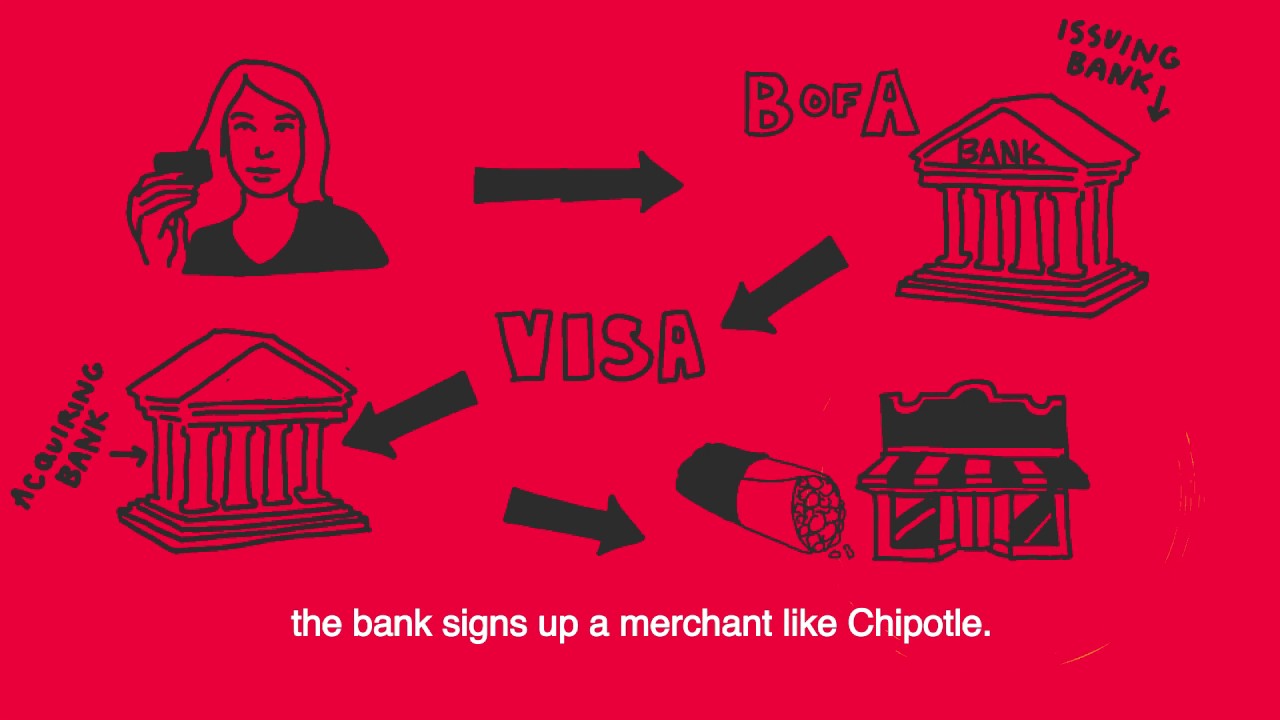
A Brief History of Credit Cards (or What Happens When You Swipe)

How UPI's Bold Business STRATEGY will KILL VISA and MASTERCARD? : UPI CREDIT LINKING EXPLAINED

Educati e Finanziati 04: ti serve una carta di credito? | corso base di finanza
5.0 / 5 (0 votes)
