10 Architecture Patterns Used In Enterprise Software Development Today
Summary
TLDRThis video script delves into the critical realm of enterprise-scale software architecture, exploring seven essential patterns including Layered, Pipe-Filter, Client-Server, MVC, Event Bus, Microservices, and Broker patterns. It highlights their applications, advantages, and potential pitfalls, offering insights into designing efficient, scalable systems suitable for diverse enterprise needs. The script also touches on P2P, Blackboard, and Master-Slave patterns, emphasizing their unique roles in solving complex problems and enhancing system robustness.
Takeaways
- 🏢 Architectural patterns are essential for designing large enterprise systems to meet functionality and quality requirements.
- 📚 The layered pattern is a common architecture with four tiers: presentation, application, business logic, and data access layers, suitable for simple applications with budget and time constraints.
- 🔄 The pipe-filter pattern is used for processing sequences, where each filter performs a specific function, commonly used in compilers.
- 🔗 The client-server pattern involves a service requester and provider, often communicating over a network, with the potential disadvantage of a server being a single point of failure.
- 🖥️ The model-view-controller pattern separates application functionality into model, view, and controller components, used widely in web frameworks like Django and Rails.
- 🚦 The event bus pattern is for distributed systems handling high-volume events, with components like event source, listener, channel, and bus, but may face scalability issues.
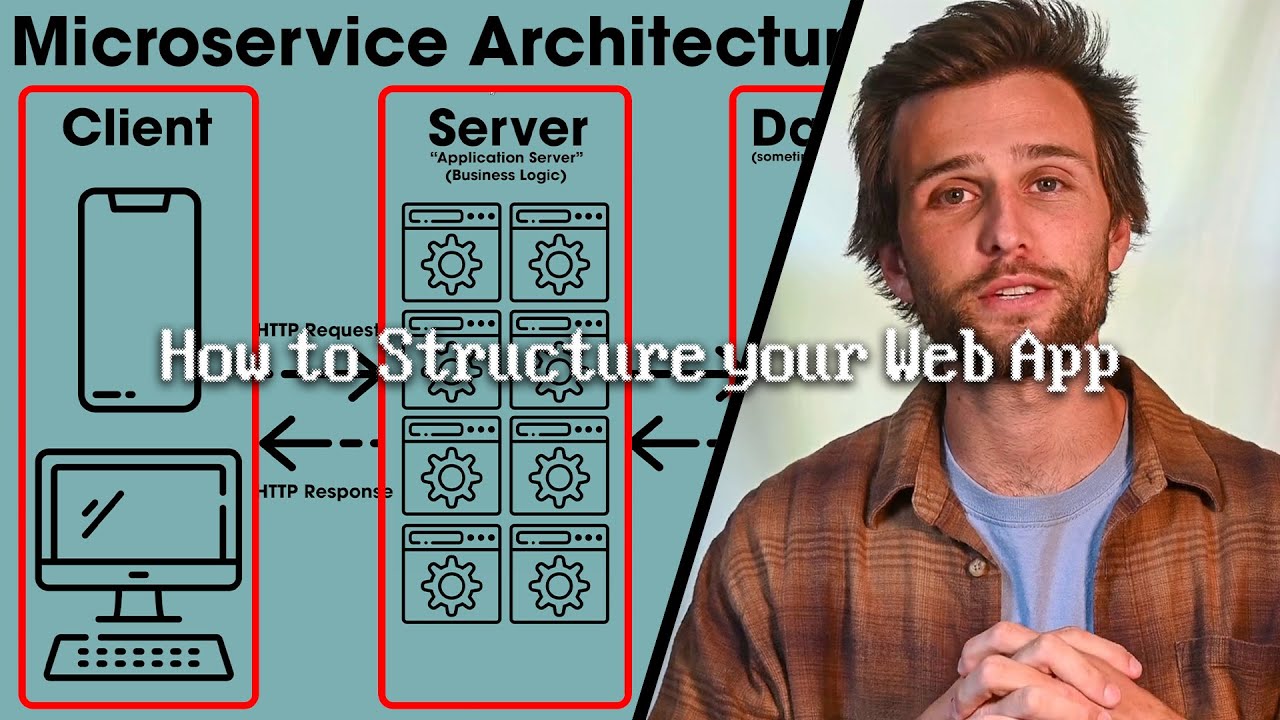
- 🛠️ Microservices architecture is for building applications as independently deployable and scalable services, each with its own API, suitable for complex enterprise apps.
- 🧩 The broker pattern structures distributed systems with decoupled components that interact through a broker, used in message broker software like Apache Kafka.
- 🔄 The peer-to-peer pattern supports decentralized computing with peers acting as both clients and servers, used in file-sharing networks and cryptocurrency.
- 📋 The blackboard pattern is for problems without deterministic solutions, involving a global memory, specialized modules, and a control component, used in speech recognition and signal interpretation.
- 🔄 The master-slave pattern involves a master distributing work to identical slave components, used in database replications where the master is the authoritative source.
Q & A
What is an architectural pattern according to Wikipedia?
-An architectural pattern is a general, reusable solution to a commonly occurring problem in software architecture within a given context.
What are the four tiers of layers in the Layered Pattern?
-The four tiers of layers in the Layered Pattern are the presentation layer, application layer, business logic layer, and data access layer.
What is the main advantage of using the Layered Pattern in software development?
-The main advantage of using the Layered Pattern is that a lower layer can be used by different higher layers, which is beneficial for building general desktop applications and relatively simple web apps.
How does the Pipe-Filter Pattern handle a sequence of processing steps in an enterprise application?
-The Pipe-Filter Pattern divides a larger processing task into a sequence of smaller independent processing steps or filters that are connected by channels or pipes.
What are the two main components of the Client-Server Pattern?
-The two main components of the Client-Server Pattern are the client, which is the service requester, and the server, which is the service provider.
What is the Model-View-Controller (MVC) Pattern and its purpose in application development?
-The MVC Pattern separates application functionality into three components: the model, which contains the core functionality and data; the view, which displays the information to the user; and the controller, which handles user input. It is used to keep the user interface functionality separate from application functionality while remaining responsive to user input or data changes.
What are the four major components of the Event Bus Pattern?
-The four major components of the Event Bus Pattern are the event source, event listener, channel, and event bus.
How does the Microservices Architecture help in managing modern enterprise applications?
-The Microservices Architecture helps by building applications as a collection of independently deployable and scalable services, each with its own API boundary, allowing for efficient support and deployment.
What is the Broker Pattern and its role in distributed systems?
-The Broker Pattern is used to structure distributed systems with decoupled components that interact by remote service invocations. A broker component coordinates communication among components, allowing for dynamic changes in the system.
How does the Peer-to-Peer (P2P) Pattern support decentralized computing?
-The P2P Pattern supports decentralized computing by allowing individual components, known as peers, to function both as clients requesting services and as servers providing services, with the ability to dynamically change roles over time.
What is the Blackboard Pattern and its components?
-The Blackboard Pattern is useful for problems without deterministic solution strategies and consists of three main components: the blackboard, a structured global memory; knowledge sources, specialized modules; and a control component that selects, configures, and executes modules.
What is the Master-Slave Pattern and its application in database replication?
-The Master-Slave Pattern consists of a master component that distributes work among identical slave components and computes a final result from the results returned by the slaves. It is used in database replications where the master database is the authoritative source, and the slave databases are synchronized to it.
Outlines

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنMindmap

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنKeywords

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنHighlights

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنTranscripts

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنتصفح المزيد من مقاطع الفيديو ذات الصلة

Top 5 Most Used Architecture Patterns

Software Architecture | Architectural patterns | Architecture vs Design pattern

Microservices with Databases can be challenging...

Собеседование о микросервисах | CQRS, Event Sourcing | Circuit Breaker, Retry | Мониторинг | Jetbulb

Introduction to System Design - MVC and Three-Tier Architecture
Everything You NEED to Know About WEB APP Architecture
5.0 / 5 (0 votes)
