UNIT-III Public key cryptography
Summary
TLDRThis video discusses the fundamentals of cryptography, particularly focusing on the differences between public and private keys. It explains how encryption and decryption work, highlighting the importance of security in communication. The content covers the use of public-key cryptography for verifying messages and authenticating users, and addresses the challenges of sharing cryptographic keys securely. The video also introduces concepts such as signature generation and authentication, and the role of private and public keys in ensuring confidentiality. It concludes with practical examples and a call to action for viewers to subscribe for further insights.
Takeaways
- 😀 Public and private keys are essential in cryptography for secure communication.
- 😀 The process involves encrypting messages with a public key and decrypting them with a private key.
- 😀 Cryptography ensures confidentiality, allowing secure communication even in public places.
- 😀 A major advantage of public key cryptography is that the encryption and decryption process is asymmetric.
- 😀 The use of private keys in cryptography is crucial for data integrity and authenticity.
- 😀 The concept of key distribution is a challenge in private cryptography systems, as public keys need to be securely shared.
- 😀 The script explains the difference between public and private keys and their role in encryption and decryption.
- 😀 Cryptography is a significant advancement in ensuring secure digital communication and is used in real-world applications.
- 😀 The importance of encryption algorithms, such as RSA, in protecting information is highlighted in the script.
- 😀 The video encourages viewers to subscribe and follow through with practical applications of cryptography concepts for better understanding.
Q & A
What is the main topic discussed in the script?
-The main topic discussed in the script is Cyber Security, with a focus on Public and Private Key Cryptography.
What is the role of public and private keys in cryptography?
-Public and private keys are used in cryptography for secure communication. The public key is used for encryption, while the private key is used for decryption.
What is the significance of 'Private Key Cryptography' in the script?
-Private Key Cryptography is significant because it ensures that only the intended recipient, who possesses the private key, can decrypt the message. This provides confidentiality.
How does public key cryptography differ from private key cryptography?
-Public key cryptography uses a pair of keys: a public key for encryption and a private key for decryption. In contrast, private key cryptography uses the same key for both encryption and decryption.
What is the purpose of the 'subscription' references in the script?
-The 'subscription' references appear to be part of a metaphor or call to action in the script, encouraging viewers to engage with the content, such as subscribing to a channel.
What does the term 'encryption' refer to in the context of the script?
-Encryption in the context of the script refers to the process of converting a message into a secure format using an encryption algorithm, making it unreadable to anyone who does not have the decryption key.
Why is public key cryptography considered secure?
-Public key cryptography is considered secure because the encryption key (public key) can be freely distributed, but only the corresponding private key can decrypt the message, ensuring confidentiality.
What are the potential drawbacks of private key cryptography mentioned in the script?
-A drawback of private key cryptography mentioned is the difficulty in securely sharing the private key, as anyone who has access to it can decrypt the message.
How does the 'signing' process work in cryptography according to the script?
-In cryptography, signing involves using a private key to create a digital signature for a message, which can be verified by others using the corresponding public key. This ensures the integrity and authenticity of the message.
What is the 'problem with distribution' in private key cryptography as mentioned in the script?
-The 'problem with distribution' refers to the challenge of securely sharing the private key between parties without it being intercepted or compromised during transmission.
Outlines

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنMindmap

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنKeywords

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنHighlights

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنTranscripts

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنتصفح المزيد من مقاطع الفيديو ذات الصلة
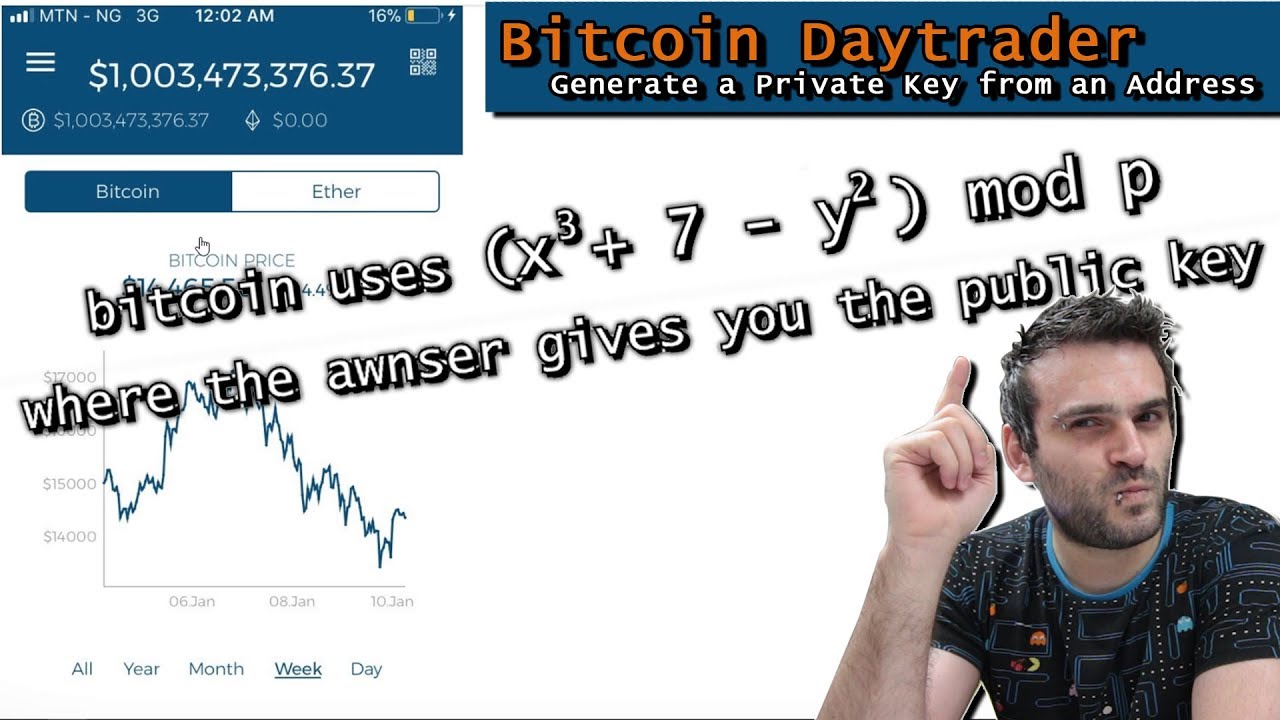
How to Generate a Private Key from a Bitcoin watch only address

Public Key Infrastructure - CompTIA Security+ Sy0-701 - 1.4

How prime numbers protect your privacy #SoME2

Symmetric and Asymmetric Cryptography - SY0-601 CompTIA Security+ : 2.8

CISSP Cyber Security: PKI Public Key Infrastructure: Digital Certificate #publickey #sslcertificates

CompTIA Security+ Full Course: Public Key Infrastructure (PKI)
5.0 / 5 (0 votes)
