Is your cloud-based storage at risk of being hacked?
Summary
TLDRIn the wake of celebrity phone hacks, the script discusses the vulnerability of personal data stored on the cloud. Senior editor Dan Aran suggests two-factor authentication as a primary defense, noting its availability on platforms like Gmail and Apple. He warns that even deleted data might persist due to copies or backups, urging users to assume their information could be retained indefinitely.
Takeaways
- 📱 **Vulnerability of Cloud Data**: The information we store on the cloud is potentially vulnerable, especially for celebrities who are actively targeted.
- 🔍 **Multiple Devices Involved**: The hacker may have used different devices to gather the photos, indicating a broad attack surface.
- 👥 **Group Effort**: It's possible that a group, rather than a single individual, is behind the hacking, compiling data over time.
- 🔒 **Two-Factor Authentication**: Enabling two-factor authentication is a crucial step in protecting your accounts, as it requires physical access to your device to make significant changes.
- 🔑 **Service Vulnerabilities**: No service is completely immune; vulnerabilities are found and patched regularly, such as the Apple lock incident earlier in the year.
- 🌐 **Global Threats**: Services like Gmail have faced targeted attacks, especially in certain countries, emphasizing the global nature of cyber threats.
- 🚫 **Deletion Limitations**: Even if you delete something from the cloud, there's a chance that copies exist elsewhere, so assume data may persist.
- 🔎 **Continuous Monitoring**: Users should be vigilant and monitor their accounts for any unusual activity, as the threat is ongoing.
- 📈 **Evolution of Cybercrime**: Cyber threats evolve, and hackers are becoming more sophisticated, requiring users to stay updated on security measures.
- 🌐 **Cloud Services**: While cloud services are beneficial for data backup and accessibility, they introduce new vulnerabilities that need to be managed.
Q & A
How vulnerable is the information we store on the cloud?
-The information stored on the cloud is potentially vulnerable since it can be accessed from multiple places and shared with many people, increasing the risk of unauthorized access.
Are celebrities more at risk of cloud data breaches?
-Celebrities might be at higher risk due to the fact that people are actively looking for their information, making them a more attractive target for hackers.
How did the hacker gain access to the system in the discussed case?
-It's unclear if it was one person or a group, but it seems that the hacker(s) collected photos over a period of time from different devices before making them public.
What is the primary step to protect oneself from cloud data breaches?
-The primary step is to enable two-factor authentication wherever possible, which adds an extra layer of security by requiring a physical device to make significant changes to an account.
Is there any company that is more protected against cloud data breaches than others?
-While no company is completely immune, they can differ in their level of protection. Companies like Apple and Gmail have had exploits but have also implemented measures like two-factor authentication to improve security.
What was the exploit Apple had earlier in the year as mentioned in the script?
-Apple had an exploit where phones were hijacked by making them think they were lost, locking them, and then demanding payment to unlock them.
How has Gmail addressed security concerns in the face of hacking attempts?
-Gmail has added two-factor authentication to slow down hackers and prevent unauthorized access, especially in regions where government hacking is more prevalent.
Is it possible to completely delete something from the cloud?
-While you can delete something from the cloud, there's a chance that someone might have a copy of it, so it's advised to assume that a backup might exist.
What is the implication of the statement 'it's almost impossible to completely bulletproof life'?
-It implies that due to the vast amount of information we share and the numerous cloud services we use, it's challenging to secure everything completely against breaches.
What is two-factor authentication and how does it help protect cloud data?
-Two-factor authentication is a security measure that requires a second form of verification, such as a text message code, in addition to a password. It helps protect cloud data by ensuring that even if a password is compromised, an attacker would also need access to the physical device to make significant changes.
What advice does Dan Aran give for safely storing information on the cloud?
-Dan Aran advises using two-factor authentication and being cautious about what information is uploaded to the cloud, understanding that once something is online, it can be difficult to ensure complete deletion.
Outlines

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنMindmap

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنKeywords

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنHighlights

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنTranscripts

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنتصفح المزيد من مقاطع الفيديو ذات الصلة
Where ESI is Stored and How it is Retrieved: Module 2 of 5

Certificateless public integrity checking of group shared data on cloud storage | Java IEEE Project

13 Mengenal Internet Dasar

Should You Use Fingerprint Unlock?
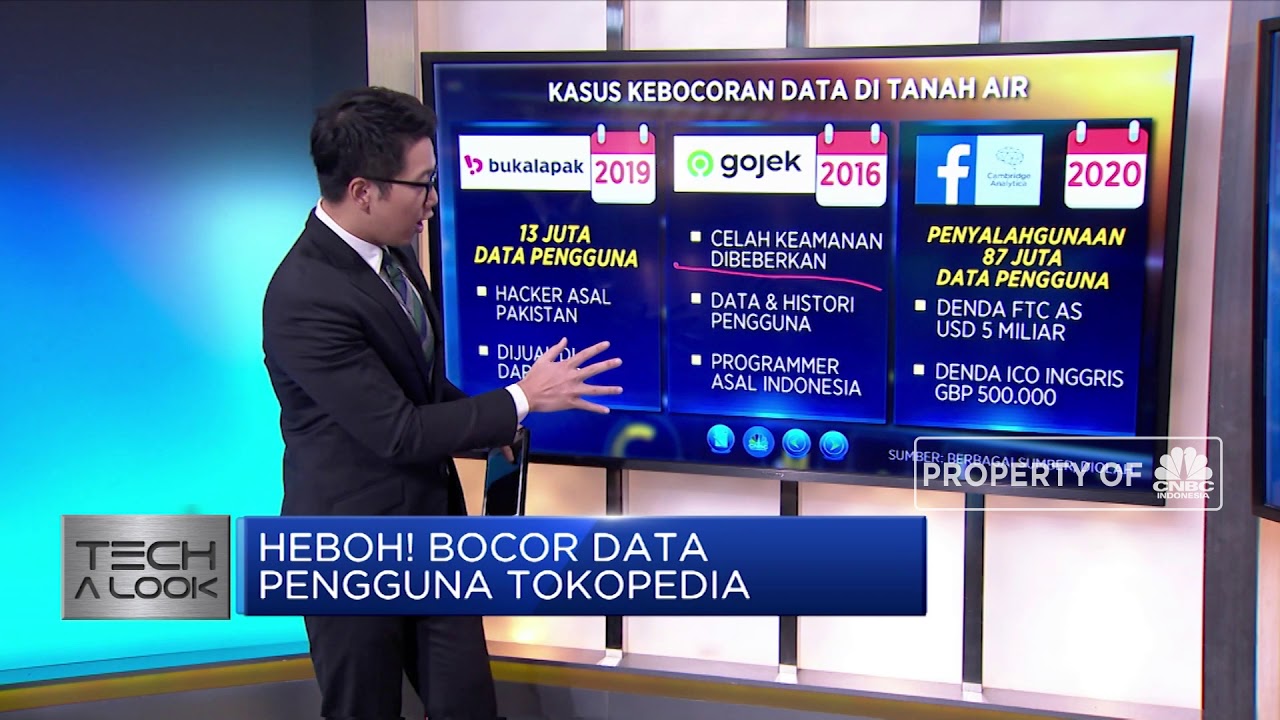
Heboh! Kebocoran Data Pengguna Tokopedia

. [Análise de Dados] Módulo 2 - Onde os Dados são Armazenados? aula 1
5.0 / 5 (0 votes)
