MD5 Algorithm | What Is MD5 Algorithm? | MD5 Algorithm Explained | Network Security | Simplilearn
Summary
TLDRThis video from Simply Learn explores the MD5 hash algorithm, a widely-used method for data scrambling. It explains hashing principles, the origin and methodology of MD5, and its application in password storage and data integrity verification. Despite known vulnerabilities, MD5 remains significant for non-cryptographic checksums. The video outlines the steps of the MD5 algorithm, emphasizing its fixed 128-bit digest output and the importance of preventing hash collisions for secure data handling.
Takeaways
- 🔒 The MD5 algorithm is a widely used cryptographic hash function that produces a 128-bit hash value.
- 🌐 MD5 was designed as an improvement over MD4 and is still used in various environments despite known vulnerabilities.
- 🔑 Hashing is an irreversible process that scrambles data beyond recognition, unlike encryption which is reversible.
- 💼 MD5 is used for password storage on websites, ensuring that plain text passwords are not stored, thus enhancing security.
- 🔍 Hashing is also used to verify data integrity, helping to ensure that files have not been corrupted during transmission.
- 🛠️ The MD5 algorithm involves several steps including padding the input message, initializing buffers, and performing rounds of operations on sub-blocks.
- 🔄 Circular shifts are used in MD5 to increase complexity and randomness, helping to prevent hash collisions.
- 📊 MD5 produces a fixed-size digest, which simplifies storage and comparison, and is easier to manage on servers.
- 🚫 Despite its widespread use, MD5 has been deprecated for cryptographic purposes due to security flaws that have been discovered.
- 💡 MD5 is still used for non-cryptographic checksums to verify data integrity and detect unintentional data corruption.
Q & A
What is the primary purpose of hashing?
-The primary purpose of hashing is to scramble a piece of information or data beyond recognition using hash functions, which perform mathematical operations on the plain text. The resulting hash value is irreversible and cannot be decrypted back to the original value.
How does hashing differ from encryption?
-Hashing is irreversible and does not require a decryption key to convert the hash value back to the original data, whereas encryption is reversible and requires a decryption key to decrypt the data.
What is the MD5 hashing algorithm?
-The MD5 hashing algorithm is a one-way cryptographic function that accepts a message of any length and returns a fixed length digest value of 128 bits, used for authenticating the original message.
Why was MD5 designed?
-MD5 was designed by Ronald Rivest as an improvement to the MD4 algorithm, originally intended for use as a secure cryptographic hash algorithm to authenticate digital signatures.
What is the significance of the 128-bit digest size in MD5?
-The 128-bit digest size in MD5 ensures that the output is always the same length, making it easier to compare when verifying the digest, consume less disk storage, and be easier to remember and reiterate.
How does MD5 prevent hash collisions?
-MD5 prevents hash collisions by creating a drastic difference in the digest even with a slight change in the plaintext, thus maintaining the uniqueness of the hash for each individual input.
What is the process of padding in MD5 hashing?
-In MD5 hashing, padding involves making the plaintext compatible with the hash function by ensuring the size is 64 bits short of a multiple of 512. This is done by adding a '1' bit followed by zeros to round out the extra characters.
What are the four buffers or registers used in MD5 hashing?
-The four buffers or registers used in MD5 hashing are A, B, C, and D, each of which is 32 bits and stores values for the sub-blocks during the hashing process.
How does the MD5 algorithm ensure the randomness of the hash?
-The MD5 algorithm ensures randomness by using a non-linear process with different formulas for each of the four rounds, and by employing a random array of 64 constant values for each block iteration.
What are the advantages of using MD5 for password storage?
-Using MD5 for password storage prevents plaintext passwords from being stored, protecting user privacy in the event of a data breach. It also ensures that the database security is enhanced as the size of all hash values will be the same.
How does MD5 help in verifying data integrity?
-MD5 helps in verifying data integrity by generating a hash digest when a file is uploaded. This digest is then compared to the one calculated after download to ensure the data was not corrupted during transit.
Outlines

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنMindmap

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنKeywords

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنHighlights

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنTranscripts

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنتصفح المزيد من مقاطع الفيديو ذات الصلة
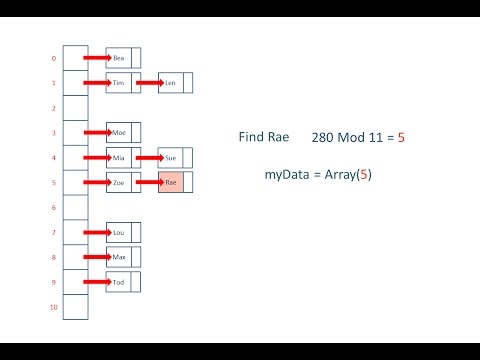
Hash Tables and Hash Functions

49. OCR A Level (H446) SLR9 - 1.3 Hashing

SHA 256 | SHA 256 Algorithm Explanation | How SHA 256 Algorithm Works | Cryptography | Simplilearn
How do computers elect leaders? | Consensus and Leader Election Explained

L-6.1: What is hashing with example | Hashing in data structure

157. OCR A Level (H446) SLR26 - 2.3 Dijkstra's shortest path
5.0 / 5 (0 votes)
