FortiSIEM Investigation of a FortiEDR Alert | Security Information and Event Management (SIEM)
Summary
TLDRThis video demo introduces a straightforward attack and how the Foran Net SE Ops platform detects malware. It walks through the key stages of detection and response using For EDR and For Sim, showcasing how security operations identify threats like the Cash Cat ransomware. The demo explains the analysis of system logs, investigation of incidents, and artifact tracing. Additionally, it highlights the role of For Advisor, an AI assistant, in augmenting security effectiveness by providing actionable insights to analysts. The demo concludes with an emphasis on understanding and mitigating attacks.
Takeaways
- 🔍 The demo is designed to show an introductory attack, not to demonstrate evasion or sophisticated bypass techniques.
- 🛡️ Fora's SE Ops platform detects various malware attacks, including ransomware, by leaving behind artifacts for analysis.
- ⚙️ The demo uses Fora's EDR (Endpoint Detection and Response) and SIM (Security Information Management) for detecting and managing security events.
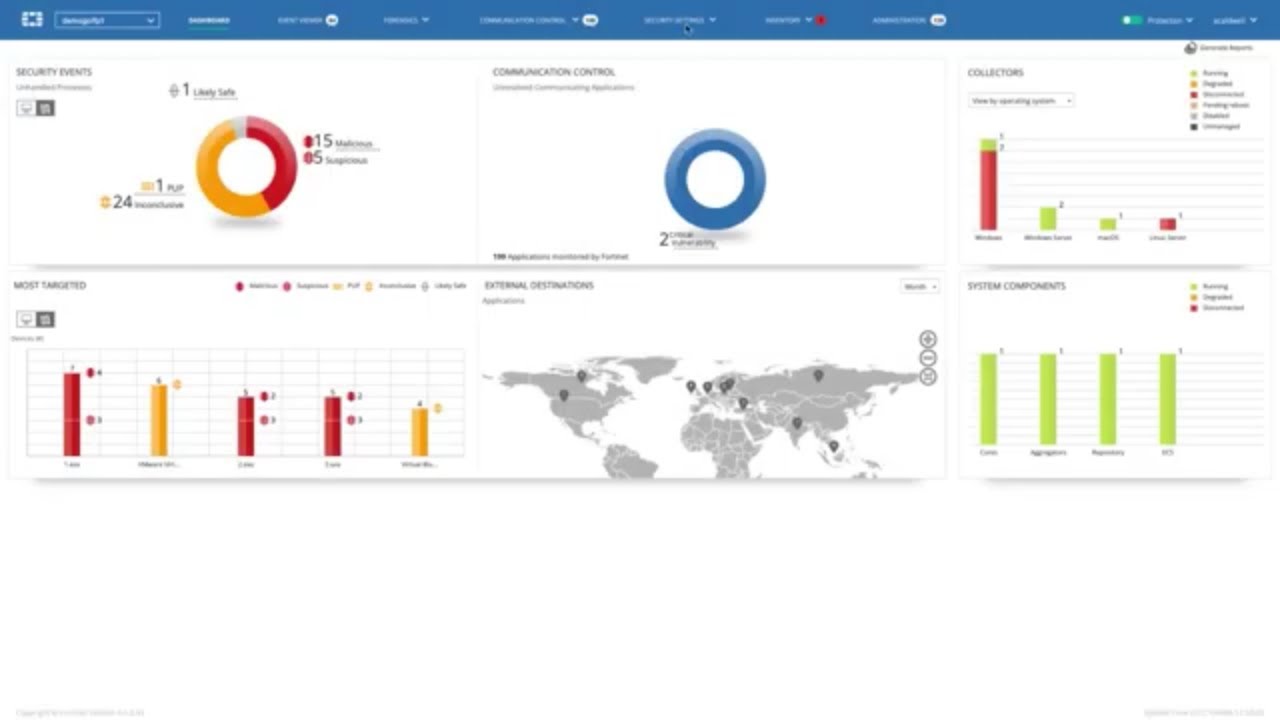
- 📊 Fora EDR's dashboard provides an overview of system security events, including targeted systems and communication activity.
- 🚨 The platform logs and categorizes security events, providing detailed information on attacking processes, devices, and incident timelines.
- 💻 In this scenario, a ransomware attack called 'cash cat' was detected through Fora EDR's security policies.
- 📥 Detection logs are forwarded to Fora SIM for centralized incident notifications, including email alerts and integration with firewalls.
- 🔧 Security operators can configure custom responses, such as isolating clients or deleting malicious files, in the EDR playbook section.
- 🕵️♂️ The platform provides detailed forensics for threat hunting, showing the processes, files affected, and policy rules triggered.
- 📈 Fora SIM's analytics offer a timeline of incidents, making it easier for SOC (Security Operations Center) analysts to investigate attacks and mitigate threats.
Q & A
What is the primary purpose of the demo shown in the script?
-The primary purpose of the demo is to provide a straightforward introduction to detecting and addressing malware attacks using the Fora SE Ops platform, specifically focusing on Fora EDR and Fora SIM detection capabilities.
What does Fora EDR provide to help security operators pinpoint attacks?
-Fora EDR provides a dashboard that offers an at-a-glance overview of system security events, targeted systems, system communication control, external communication destinations, and the health of collectors and management.
What types of actions can be taken when Fora EDR detects an attack?
-When Fora EDR detects an attack, actions include emailing alerts, isolating the client, terminating malicious processes, deleting infected files, cleaning persistent data, blocking IP addresses with firewalls, locking users in Active Directory, and opening tickets with software ticketing systems.
How does the Fora SE Ops platform handle log data?
-The platform uses CIS logs to forward incident data to Fora SIM for centralized notifications. The logs can be filtered and analyzed to find specific events, such as those related to a ransomware attack.
How are attack events visualized in the Fora SIM platform?
-Attack events are visualized using timelines and graphical representations in Fora SIM, allowing security operators to follow the sequence of incidents and pinpoint the exact flow of the attack for further investigation.
What role does the 'Cash Cat' process play in the demo scenario?
-In the demo, 'Cash Cat' is a ransomware simulation process. Fora EDR detected it under the dynamic code file encrypter trigger and showed how it impacted files, including renaming a file to an encrypted version.
How does Fora SIM help in investigating an attack?
-Fora SIM provides detailed incident reports, including triggering events, affected processes, and related entities. It allows analysts to drill down into each incident and visualize the attack flow, making it easier to trace the origin and artifacts of the attack.
What is the role of 'Fora Advisor' in the SE Ops solution?
-Fora Advisor is an AI assistant that augments security analysts' capabilities by providing context-aware insights, threat intelligence, and actionable results directly within the product to enhance their efficiency and accuracy.
How does the timeline feature in Fora SIM contribute to incident investigation?
-The timeline feature in Fora SIM visually represents the sequence of events, allowing analysts to understand how the attack unfolded over time. It includes an animated replay option, which helps in comprehensively understanding the attack's progression.
What kinds of artifacts can security operators investigate using Fora SIM?
-Security operators can investigate various artifacts, such as processes that were started, users involved, blocked files, IP addresses, and how these elements are related to each other, offering a complete view of the attack's impact.
Outlines

此内容仅限付费用户访问。 请升级后访问。
立即升级Mindmap

此内容仅限付费用户访问。 请升级后访问。
立即升级Keywords

此内容仅限付费用户访问。 请升级后访问。
立即升级Highlights

此内容仅限付费用户访问。 请升级后访问。
立即升级Transcripts

此内容仅限付费用户访问。 请升级后访问。
立即升级浏览更多相关视频

Dewatalks: Combatting Online Gambling Malware & Others

What is dot net | .Net అంటే ఏంటి? | Vamsi Bhavani

Visual Basic Dot Net Framework Architecture in Hindi

How Does Antivirus and Antimalware Software Work?
FortiEDR - Advanced Endpoint Protection with Automated Detection and Response | Endpoint Security
How Does Agentforce Work? | Salesforce
5.0 / 5 (0 votes)
