Communications and Network Security Part 21 – Secure Voice Communications
Summary
TLDRThis lesson delves into the security of voice communications through POTS (PSTN) and VoIP. It highlights the vulnerabilities inherent in both methods, including eavesdropping and vishing, and emphasizes the importance of confidentiality. The video outlines how POTS operates, typically within PBX systems, and contrasts this with the digital advantages of VoIP. Key security challenges, such as default settings and malware risks, are discussed, along with essential protective measures like traffic segmentation, encryption, and user education. Overall, the lesson underscores the need for organizations to prioritize voice communication security to safeguard sensitive information.
Takeaways
- 📞 Voice communications are critical and can contain highly sensitive information.
- 📡 POTS (Public Switched Telephone Network) is the traditional method for voice communication.
- 💻 VoIP (Voice over Internet Protocol) allows digital voice communication over the internet, reducing costs and enhancing security when configured properly.
- 🔒 Voice communications are vulnerable to attacks such as interception, eavesdropping, and tapping, especially in POTS setups.
- 🛡️ VoIP security starts with effective risk management during the design phase, addressing default security settings and configurations.
- 📶 VoIP devices often use wireless connections, making strong access controls essential to protect encrypted voice traffic.
- 🦠 Malware and network attacks pose significant risks to VoIP devices connected to the internet.
- 👂 Eavesdropping is a risk for any traffic traveling over networks, which can be captured by malicious actors.
- 📞 Vishing involves phone scams where attackers impersonate trusted individuals to extract sensitive information.
- 🔗 Organizations should separate voice traffic from data traffic to protect against common attacks and enhance performance.
Q & A
What are the two main methods of voice communication discussed in the lesson?
-The two main methods of voice communication discussed are POTS (Public Switched Telephone Network) and VoIP (Voice over Internet Protocol).
How does POTS function in voice communications?
-POTS functions by converting analog voice signals into electrical signals, which are then transmitted through a network of switches to connect calls to the intended recipient.
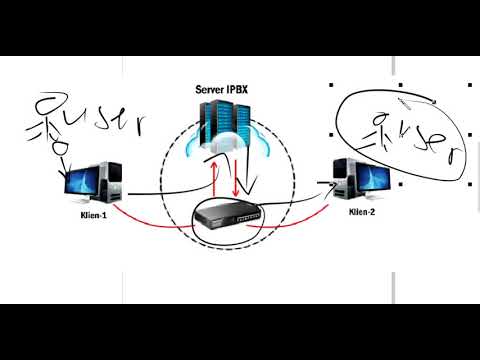
What is a PBX and why is it used in organizations?
-A PBX, or Private Branch Exchange, is used in organizations to manage phone access to and from the provider's phone service network, especially when handling multiple phone lines.
What are some vulnerabilities associated with both POTS and VoIP?
-Both POTS and VoIP are vulnerable to attacks such as call interception, eavesdropping, tapping, malware infections, and vishing (voice phishing).
What advantages does VoIP offer over POTS?
-VoIP offers advantages such as reduced costs by eliminating long-distance charges and improved security features when properly configured.
What are some key security challenges organizations face when using VoIP?
-Key security challenges for VoIP include managing default security settings, ensuring strong access controls for Wi-Fi, preventing malware infections, and protecting against eavesdropping and man-in-the-middle attacks.
How can organizations enhance the security of their VoIP systems?
-Organizations can enhance VoIP security by segmenting voice and data traffic, using VLAN access control lists, encrypting Wi-Fi networks, implementing NAT, and regularly monitoring for anomalies.
What is vishing and how does it pose a threat to organizations?
-Vishing is a form of phishing that uses phone calls or voice messages to trick employees into providing sensitive information or transferring funds, typically by impersonating an authority figure.
Why is it important to separate voice traffic from data traffic?
-Separating voice traffic from data traffic helps protect voice systems from common attacks against data networks and improves overall voice performance.
What role does user education play in securing VoIP communications?
-User education is crucial because, despite strong security measures, residual risks remain. Users must be aware of potential threats and exercise caution when using VoIP phones.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)