Managing access for Cymbal Superstore’s cloud solutions
Summary
TLDRThe video script explains the role of an Associate Cloud Engineer at Cymbal Superstore, focusing on managing Identity and Access Management (IAM) in Google Cloud. It outlines key tasks, including configuring service accounts, assigning permissions, and managing virtual machines. Using a supply chain app example, it demonstrates how to create and attach a service account to a Compute Engine virtual machine, allowing machine-to-machine communication. The script highlights the importance of both authorization and authentication in managing user and service accounts, essential skills for Associate Cloud Engineers working with Google Cloud.
Takeaways
- 😀 An Associate Cloud Engineer at Cymbal Superstore configures and manages IAM access and service accounts in Google Cloud.
- 🔒 Managing Identity and Access Management (IAM) is a core responsibility, crucial for controlling access within cloud projects.
- 🛠 Familiarity with service accounts and best practices for managing them is essential for the role.
- 🧾 The ability to view audit logs when required is an important skill for cloud engineers.
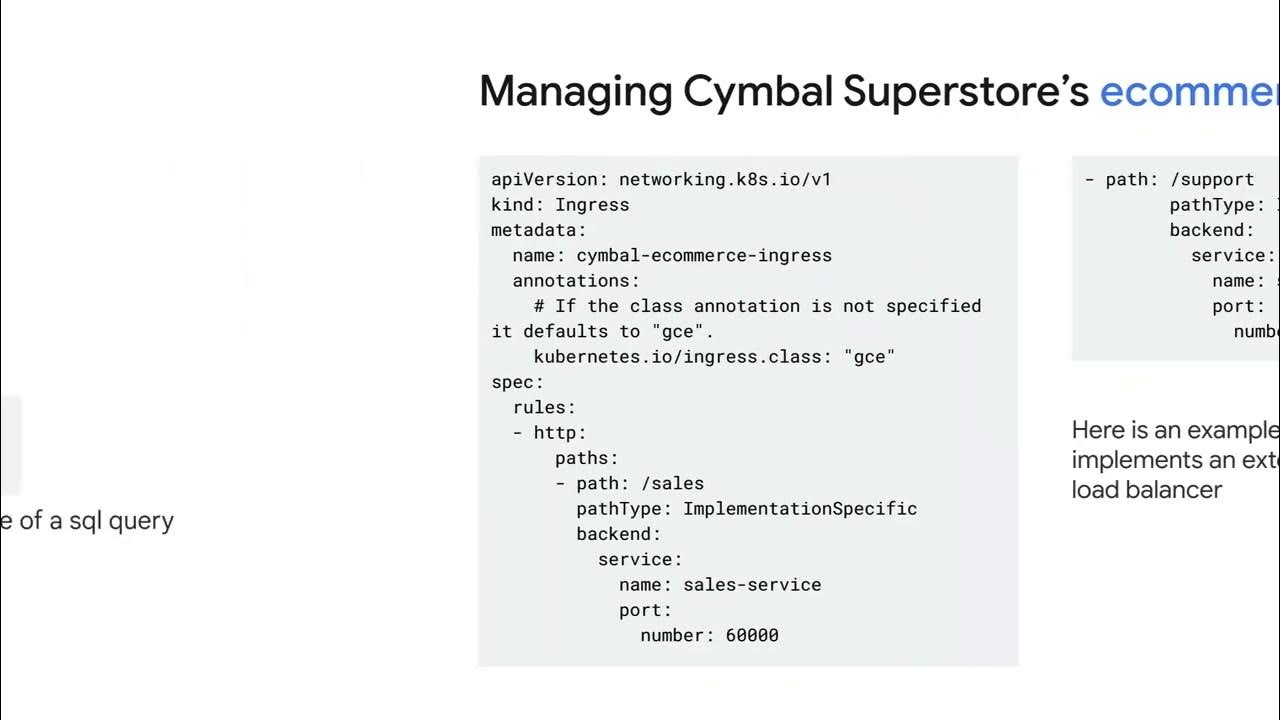
- 💡 The supply chain app at Cymbal Superstore uses a LAMP stack and runs on Google Compute Engine virtual machine instances.
- 🛠 The app communicates with Cloud SQL to update inventory levels via a service account attached to the virtual machine.
- ⚙️ To set up a service account, the first step is to create the service account and assign appropriate permissions.
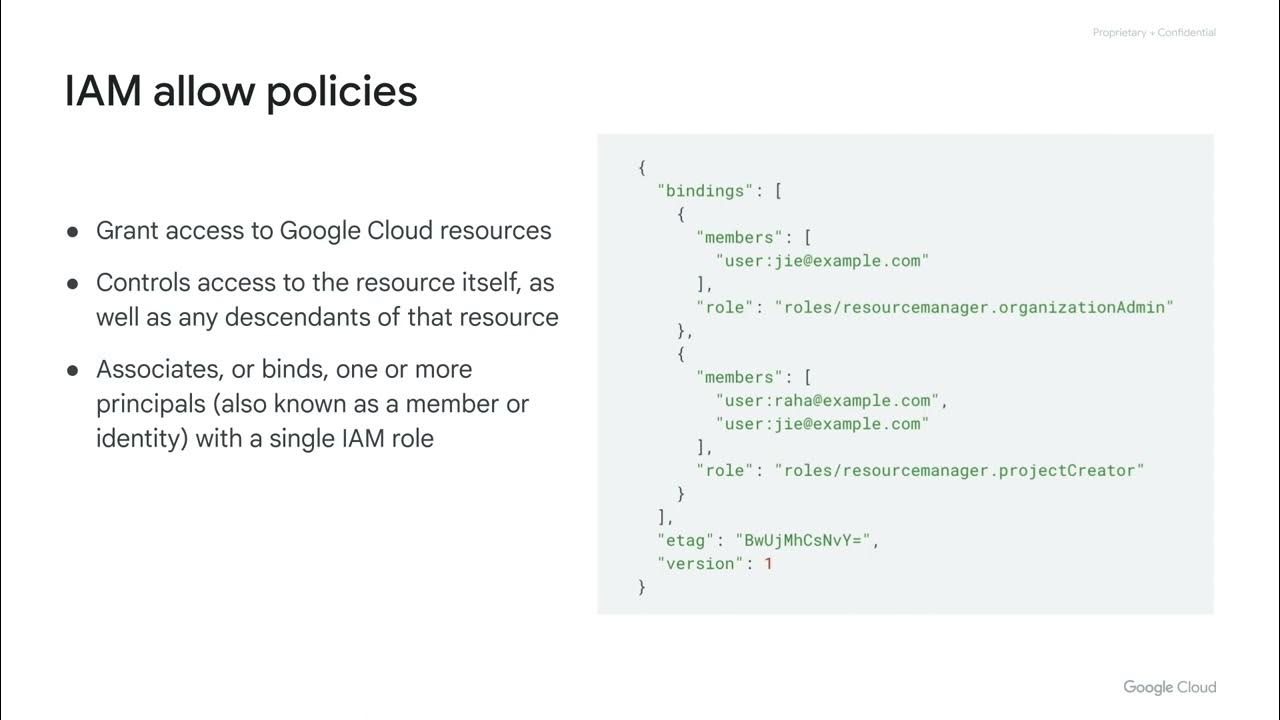
- 🔑 Permissions must be assigned to the service account for it to perform specific tasks, such as acting as a Cloud SQL instance user.
- 📋 Service accounts allow virtual machines and apps running on them to inherit permissions granted to the account.
- 🔐 Both authorization and authentication are key aspects of managing user and service accounts in Google Cloud.
Q & A
What role does an Associate Cloud Engineer play at Cymbal Superstore?
-An Associate Cloud Engineer at Cymbal Superstore configures and manages IAM access and service accounts in Google Cloud, ensuring that resources and applications have the correct permissions and secure access.
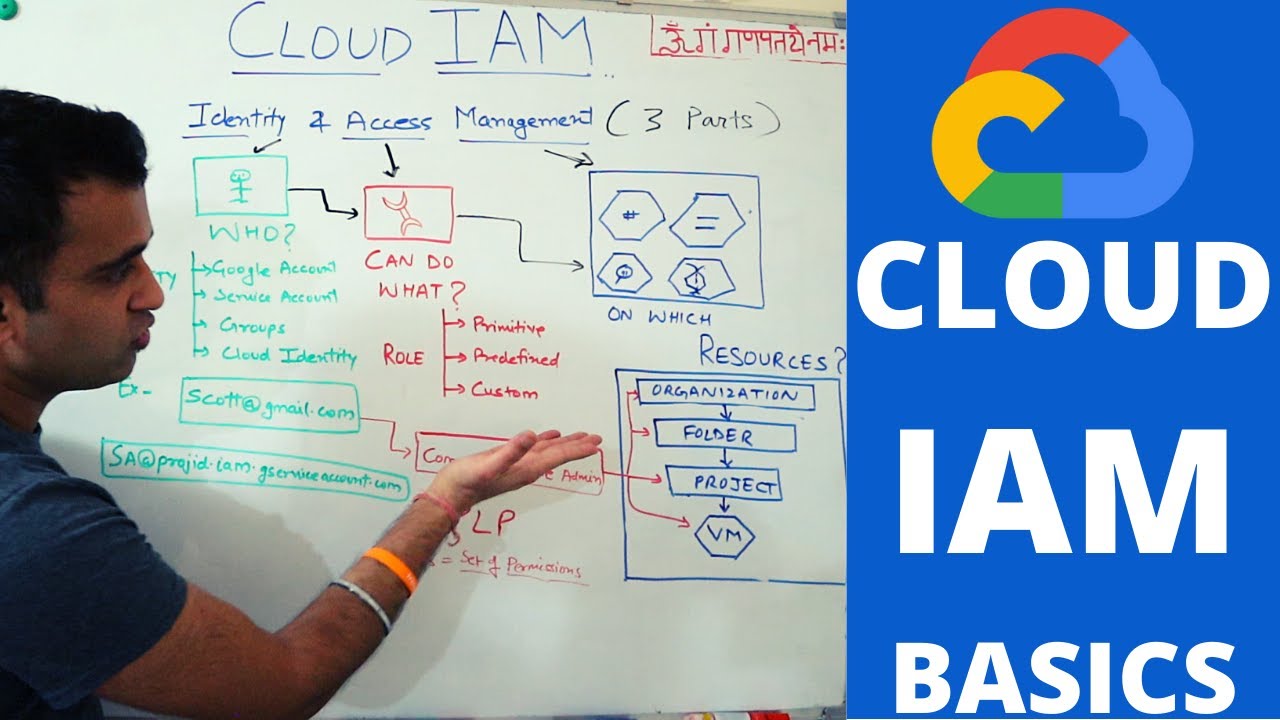
What are the key skills required for managing Identity and Access Management (IAM) in Google Cloud?
-Key skills include managing IAM permissions, understanding roles, configuring service accounts, and being able to view audit logs to track access and activities.
How does Cymbal Superstore’s supply chain app communicate with Cloud SQL?
-The supply chain app uses a service account attached to a Google Compute Engine virtual machine (VM), which enables the app to securely communicate with Cloud SQL and update inventory levels.
What is the purpose of a service account in Google Cloud?
-A service account is used for machine-to-machine communication, allowing applications running on resources like VMs to access other Google Cloud services with the assigned permissions.
What are the steps to create a service account in Google Cloud?
-To create a service account: 1) Go to the IAM menu of the project, 2) Select 'Create Service Account', 3) Name the account and note the associated email address, and 4) After creation, manage permissions for the account.
How do you assign permissions to a service account?
-Permissions are assigned by selecting 'Manage Permissions' from the actions dialog, searching for the necessary permissions (e.g., Cloud SQL instance user), and associating them with the service account.
How is a service account attached to a virtual machine (VM) in Google Cloud?
-When creating or configuring a VM, you can attach a service account in the 'Identity and API access' section, which enables the VM and any apps running on it to use the permissions associated with that service account.
What is the difference between authentication and authorization in the context of Google Cloud?
-Authorization refers to defining what resources a user or service account can access, while authentication is about verifying the identity of the user or service account accessing those resources.
Why is it important to view audit logs in Google Cloud?
-Audit logs provide a record of activities, including who accessed what resources and when. This is crucial for security monitoring, compliance, and identifying potential unauthorized access.
What is the significance of the email address associated with a service account?
-The email address acts as the unique identifier for the service account, which is used to assign permissions and identify the account when managing resources in Google Cloud.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video
5.0 / 5 (0 votes)