How To Configure VPNs using Cisco Packet Tracer (Overview)
Summary
TLDRThis video provides a comprehensive introduction to Virtual Private Networks (VPNs), explaining their role in securing data transmission over public networks. It covers key concepts such as encryption, data integrity, and authentication, and demonstrates how VPNs help protect privacy online. The script specifically focuses on setting up a site-to-site VPN using IPSec, explaining how this protocol ensures secure communication between two sites over an untrusted network. The video prepares viewers to configure and verify a site-to-site VPN connection, offering practical insights into the security protocols involved.
Takeaways
- 😀 A Virtual Private Network (VPN) extends a private network across a public network, allowing secure data communication as if devices were directly connected to the network.
- 😀 VPNs protect users' privacy by encrypting data and hiding IP addresses, making it more difficult for third parties to intercept or view the traffic.
- 😀 VPNs are used globally by millions of remote users to securely access corporate resources over the internet.
- 😀 Confidentiality in a VPN is achieved through encryption, which ensures that data transmitted across a public network is unreadable to unauthorized parties.
- 😀 Integrity is ensured using hashing, which allows for checking that data has not been altered during transmission.
- 😀 VPNs help with authentication by verifying the identity of users or systems before allowing data exchange.
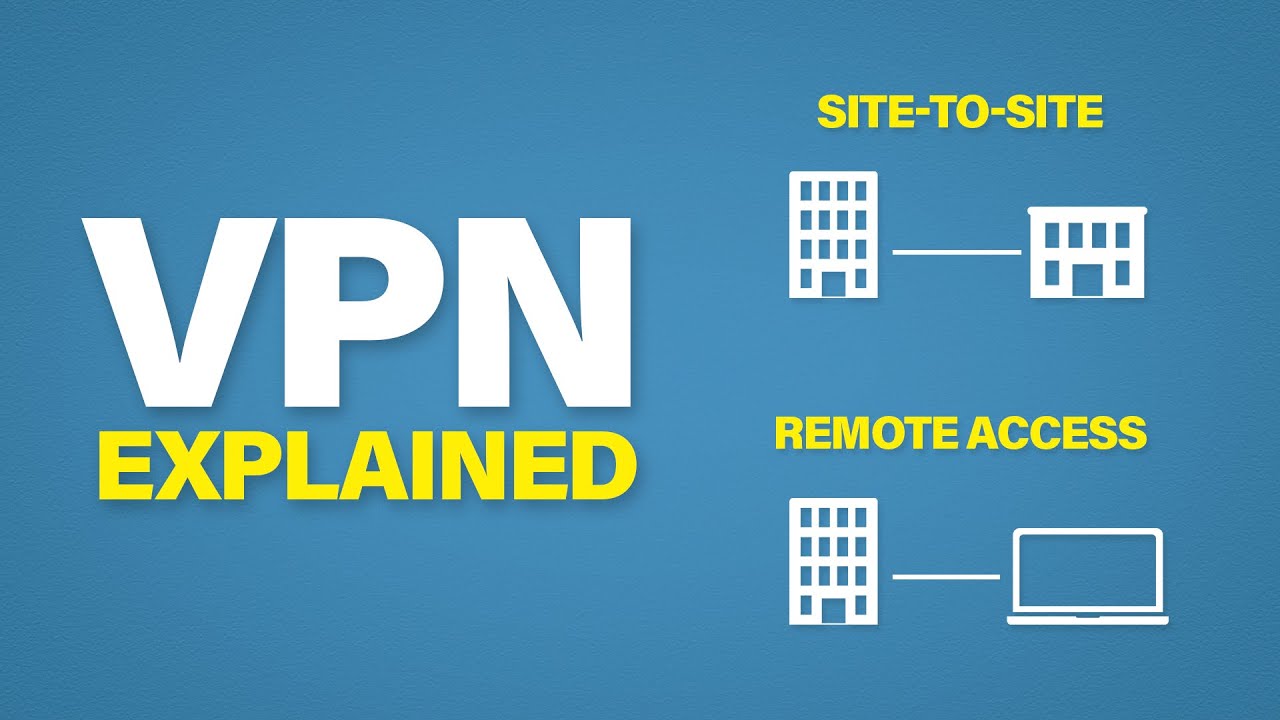
- 😀 A site-to-site VPN involves creating a secure connection (tunnel) between two separate sites (e.g., site 1 and site 3) over an untrusted network.
- 😀 IPSec (IP Security) is a protocol suite used to protect IP packets and is commonly used in site-to-site VPNs.
- 😀 IPSec operates at OSI layer 3 and offers security through a collection of protocols and algorithms designed to secure communication between devices.
- 😀 There are different methods to authenticate VPN peers, such as using pre-shared keys or private key pairs based on public key cryptography.
- 😀 The tutorial focuses on setting up a site-to-site VPN using IPSec and provides a step-by-step guide for configuration and verification.
Q & A
What is a Virtual Private Network (VPN)?
-A VPN is a service that extends a private network across a public network, allowing users to send and receive data as though their devices were directly connected to the private network.
How does a VPN help protect privacy online?
-A VPN helps protect privacy by encrypting the data, hiding the user's IP address, and preventing unauthorized parties from monitoring or accessing the transmitted data.
What is the role of encryption in a VPN?
-Encryption in a VPN ensures confidentiality by scrambling the data before it is sent across the network, making it unreadable to anyone who intercepts the data.
What is meant by data integrity in a VPN?
-Data integrity ensures that the data sent from one site is exactly the same when it reaches the destination, achieved through hashing, which verifies the data has not been altered during transmission.
How does hashing contribute to the integrity of data in a VPN?
-Hashing creates a unique value for the data being sent, which allows the recipient to verify that the data has not been tampered with or altered during transmission.
What is the purpose of authentication in a VPN?
-Authentication ensures that the data sent from one device comes from a trusted source, and that the receiver can verify the identity of the sender before accepting the data.
How do VPN peers authenticate each other?
-VPN peers can authenticate each other through methods like pre-shared keys (shared passwords) or private key pairs using public key cryptography.
What is IPSec and how is it used in VPNs?
-IPSec (IP Security) is a collection of protocols and algorithms used to protect IP packets at the OSI Layer 3. It is commonly used for site-to-site VPNs to ensure secure communication between two sites.
What is the difference between site-to-site VPNs and remote access VPNs?
-Site-to-site VPNs are used to securely connect entire networks across different locations, whereas remote access VPNs allow individual users to securely connect to a corporate network from anywhere.
Why is a site-to-site VPN configured with IPSec?
-IPSec is used in site-to-site VPNs because it provides encryption and authentication for securing the communication between two networks, ensuring the data sent between them is private and protected.
Outlines

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифMindmap

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифKeywords

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифHighlights

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифTranscripts

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифПосмотреть больше похожих видео

VLANs and VPNs - CompTIA A+ 220-1101 - 2.6

Definisi VPN, Fungsi Utama VPN, Teknologi Tunneling, Keamanan VPN - Administrasi Sistem Jaringan

What is VPN and how VPN works (Tagalog)

How VPN really works? Understand Virtual private network in 5 mins (2023)
VPNs Explained | Site-to-Site + Remote Access

What is VPN | How VPN Works 🕵️♂️| Virtual Private Network (VPN) with Real Life Examples
5.0 / 5 (0 votes)
