SAFECode Basic Practices for Secure Development of Cloud Applications 101 Quiz Part 2 p1
Summary
TLDRThe video script delves into the complexities of cloud security, focusing on key concepts such as shared responsibility models, multi-tenancy, and trusted compute pools. It emphasizes the importance of properly managing tenant data in cloud applications to prevent vulnerabilities and outlines the role of physical security measures. The script highlights relevant ISO standards for cloud security, such as ISO 27001, 27017, and 27018, which guide organizations in implementing robust information security management systems and privacy protections. By ensuring adherence to these standards, cloud customers can better safeguard their data and applications.
Takeaways
- 😀 Cloud applications typically use multi-tenancy, which allows multiple customers to share a single database while maintaining data security.
- 🔐 Two primary approaches for data sharing in multi-tenancy are shared schema and separate schema, with separate schema being the more secure option.
- 🏛️ Trusted Compute Pools (TCP) separate trusted systems from untrusted resources, ensuring higher security for sensitive applications.
- 🔍 Platform trust attributes are critical for verifying the trustworthiness of systems and determining which applications can be deployed.
- ⚙️ The Trusted Platform Module (TPM) is used to store critical trust measurements and facilitate verification of the system's security posture.
- 🛡️ Physical security considerations in cloud computing are vital, especially since infrastructure is often owned by cloud service providers.
- 📜 ISO 27001 certification is important for cloud service providers, as it ensures adherence to information security management standards.
- ☁️ ISO 27017 and ISO 27018 provide additional controls and guidelines specifically for cloud security and privacy protection.
- 🔑 When selecting cloud providers, ensure they comply with relevant ISO standards to guarantee adequate security measures are in place.
- 📝 The script concludes with a quiz section to reinforce understanding of shared responsibilities in cloud security.
Q & A
What are the primary goals of the course on secure development of cloud applications?
-The primary goals are to enhance understanding of shared security responsibilities between cloud service providers (CSPs) and customers, and to secure cloud applications effectively.
Who is the target audience for this course?
-The target audience includes software architects and program managers, but the content is beneficial for anyone involved in cloud application development.
What responsibility does the customer have regarding data classification?
-Customers must label and classify their data, especially sensitive information, and consider using encryption and tokenization to mitigate associated risks.
What role do privacy policies play in the customer's responsibilities?
-Customers need to ensure compliance with laws regarding personally identifiable information (PII) and incorporate these responsibilities into their contracts with CSPs.
How can customers secure client devices accessing cloud services?
-Customers should implement endpoint protection measures, such as security software and practices to prevent attacks like spear phishing.
Why is multi-factor authentication (MFA) crucial for securing admin accounts?
-MFA is crucial because it adds an additional layer of security beyond just passwords, helping to prevent unauthorized access to sensitive accounts.
What is the significance of role-based access control (RBAC) in cloud security?
-RBAC is significant because it manages user access based on their roles, ensuring that individuals only have access to the information necessary for their job functions.
What are the key practices for data encryption in cloud environments?
-Key practices include encrypting data both in transit and at rest, as well as implementing effective key management for securing cryptographic operations.
How does the concept of multi-tenancy affect cloud application security?
-Multi-tenancy requires applications to be designed in a way that ensures there is no data leakage between tenants, thus maintaining data confidentiality.
What are the relevant ISO standards for cloud security discussed in the course?
-The relevant ISO standards include ISO 27001 for information security management, ISO 27017 for cloud service security controls, and ISO 27018 for protecting personal data in the cloud.
Outlines

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифMindmap

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифKeywords

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифHighlights

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифTranscripts

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифПосмотреть больше похожих видео
CEH v13 Module 19 – Cloud Computing

Cloud Operating Systems Explained: Architecture, Components & Future Trends

Cyber Security Pada Cloud Platform. Part 01
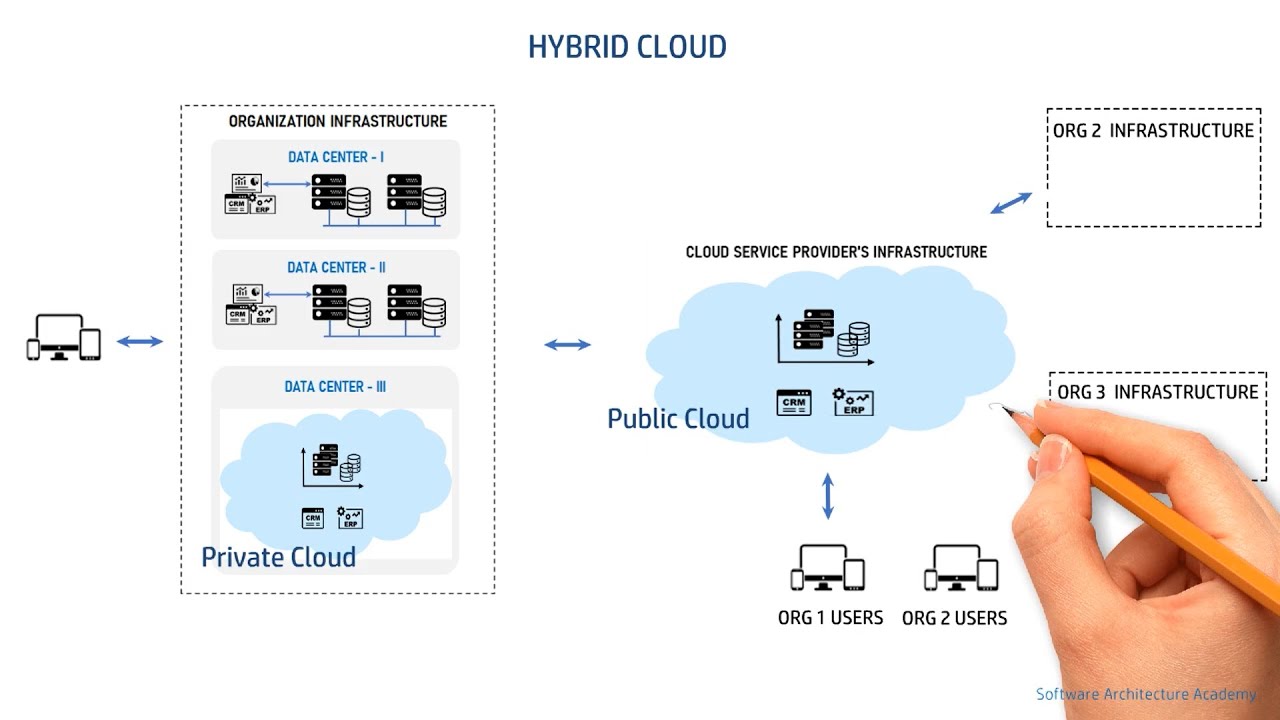
Cloud Deployment Models - Public Cloud, Private Cloud, Hybrid Cloud & Community Cloud

20 Identidade, acesso e segurança - Parte 1

A New Approach to Get Your Cloud Risks Under Control
5.0 / 5 (0 votes)
