安全
Summary
TLDRGoogle prioritizes security across its services, with nine boasting over a billion users. Their security infrastructure is layered, starting with custom-designed hardware and secure boot processes in data centers with stringent physical access controls. They encrypt inter-service communication and enhance user identity verification. Storage services apply encryption at rest, while internet-facing services use Google Front End for secure TLS connections and DoS protection. Operational security includes intrusion detection, insider risk reduction, mandatory U2F for employees, and strict software development practices, including a Vulnerability Rewards Program.
Takeaways
- 🔐 Google prioritizes security with nine of its services having over one billion users, ensuring robust security measures are in place.
- 🏢 The security infrastructure at Google is layered, starting from physical data center security to operational security processes.
- 🛠️ Google designs custom hardware including server boards, networking equipment, and a hardware security chip for enhanced security.
- 🔑 A secure boot stack is used on Google servers, incorporating cryptographic signatures for the BIOS, bootloader, kernel, and OS image.
- 🏛️ Google's data centers are designed with multiple physical security layers, and access is highly restricted to a select few employees.
- 🔒 Service deployment layer features encryption of inter-service communication, ensuring privacy and integrity across Google's infrastructure.
- 👤 Google's identity service goes beyond basic authentication, challenging users based on risk factors and supporting U2F for secondary authentication.
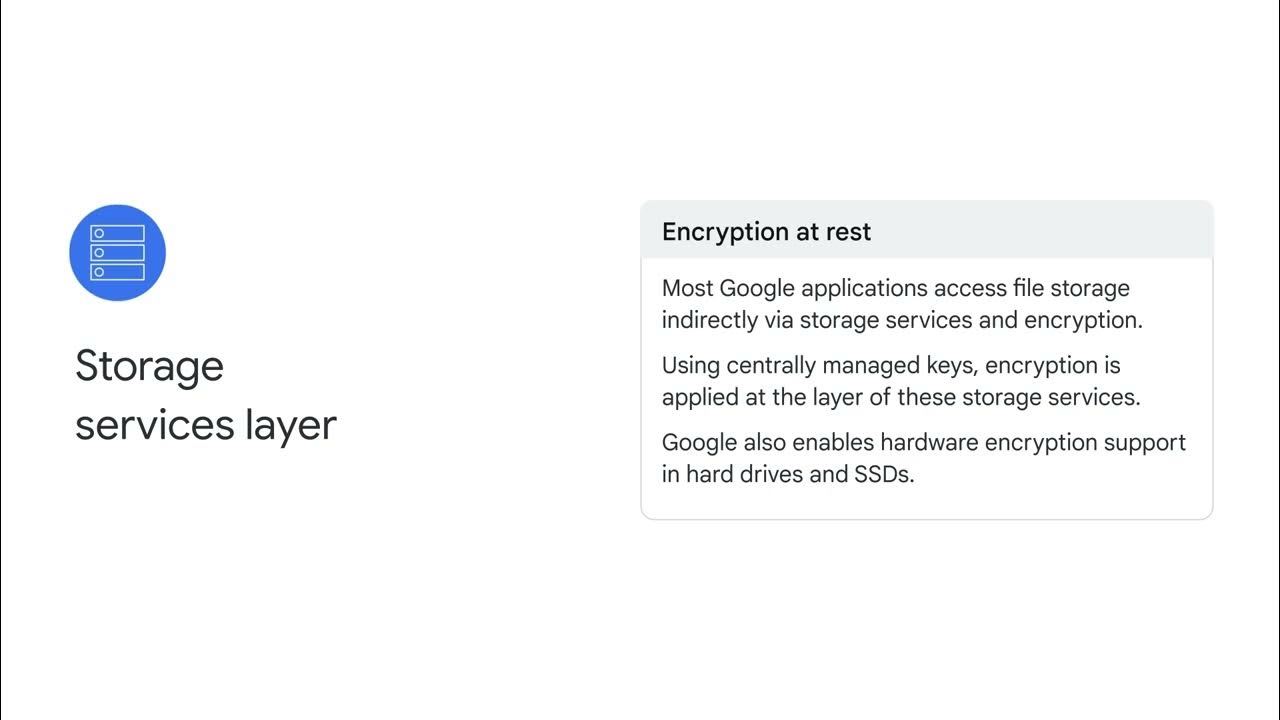
- 💾 Storage services layer includes encryption at rest, with centrally managed keys and hardware encryption support for drives and SSDs.
- 🌐 Internet communication layer involves Google Front End service for secure TLS connections and protection against Denial of Service attacks.
- 🛡️ Google's Operational security layer includes intrusion detection, insider risk reduction, mandatory U2F for employees, and stringent software development practices.
- 💰 Google offers a Vulnerability Rewards Program, incentivizing the discovery and disclosure of security bugs in their infrastructure.
Q & A
What is the significance of security in Google’s infrastructure?
-Security is a top priority for Google, especially given that nine of its services have over a billion users each. This focus on security is reflected in every aspect of its infrastructure, from the physical data centers to the software and hardware design.
How does Google ensure the physical security of its data centers?
-Google designs and builds its own data centers, incorporating multiple layers of physical security protections. Access to these data centers is highly restricted to a small number of employees, and even in third-party data centers, Google implements additional physical security measures.
What role do custom-designed hardware and chips play in Google’s security strategy?
-Google custom-designs its server boards, networking equipment, and hardware security chips. These custom components enhance security by ensuring that hardware is optimized for Google’s specific needs and is less vulnerable to external threats.
What is the purpose of Google’s secure boot stack?
-The secure boot stack ensures that Google’s server machines are booting the correct software stack by using technologies like cryptographic signatures over the BIOS, bootloader, kernel, and base operating system image.
How does Google secure inter-service communication within its infrastructure?
-Google secures inter-service communication by providing cryptographic privacy and integrity for remote procedure call (RPC) data on the network. All infrastructure RPC traffic that goes between data centers is automatically encrypted, and Google is deploying hardware cryptographic accelerators to extend this encryption to all infrastructure RPC traffic inside its data centers.
What features does Google’s central identity service provide to enhance user security?
-Google’s central identity service goes beyond simple username and password authentication by challenging users based on risk factors like device and location. It also supports secondary authentication factors, including devices based on the Universal 2nd Factor (U2F) standard.
How does Google implement encryption at rest for its storage services?
-Google applies encryption at rest using centrally managed keys at the storage services layer. Additionally, Google enables hardware encryption support in hard drives and SSDs to further secure stored data.
What is the Google Front End (GFE), and how does it contribute to internet communication security?
-The Google Front End (GFE) is an infrastructure service that ensures all TLS connections are ended using a public-private key pair and an X.509 certificate from a Certified Authority (CA). It also applies protections against Denial of Service (DoS) attacks, contributing to the security of Google services available on the internet.
How does Google detect and respond to potential security incidents?
-Google uses rules and machine intelligence for intrusion detection, providing operational security teams with warnings of possible incidents. Additionally, Google conducts Red Team exercises to improve the effectiveness of its detection and response mechanisms.
What measures does Google take to reduce insider risk within its infrastructure?
-Google limits and actively monitors the activities of employees with administrative access. It also requires the use of U2F-compatible Security Keys for employee accounts to guard against phishing attacks.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenWeitere ähnliche Videos ansehen

BEGINI PENAMPAKAN GOOGLE DATA CENTER YANG KAPASITASNYA TAK BISA KITA BAYANGKAN
Security in the cloud

Kisah Sukses Nadiem Makarim dan Gojek Indonesia - Inspirasi Bisnis

Cybersecurity for the Internet of Things (IoT)

Bizhare: Platform Securities Crowdfunding Pertama di Indonesia

Best Free Cloud Storage - 2024 Pcloud, Icedrive, Sync, Mega
5.0 / 5 (0 votes)
